 Reading Time: 5 minutes
Reading Time: 5 minutes
The arms race between cybercriminals and cybersecurity warriors is increasing at an enormous speed. Malware authors immediately react on any detected and neutralized malware with new, more sophisticated samples to bypass the freshest antimalware products. GandCrab is a bright representative of such new-generation malware.
First discovered in January 2018, this sophisticated, cunning and constantly changing ransomware has already four versions significantly distinguishing from each other. Cybercriminals constantly added new features for harder encryption and avoiding detection. The last sample Comodo malware analysts discovered has something brand-new: it utilizes Tiny Encryption Algorithm (TEA) to avoid detection.
Analyzing GandCrab is useful not as an exploration of a particular new malware, throughout some researchers called it a “New King of ransomware”. It’s a clear example of how modern malware readjusts to the new cybersecurity environment. So, let’s go deeper into the GandCrab’s evolution.
The history
GandCrab v1
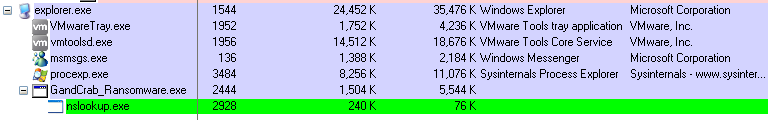
The first version of GandCrab, discovered on January 2018, encrypted users’ files with a unique key and extorted a ransom in DASH crypto-currency. The version was distributed via exploit kits such as RIG EK and GrandSoft EK. The ransomware copied itself into the“%appdata%Microsoft” folder and injected to the system process nslookup.exe.
It made the initial connection to pv4bot.whatismyipaddress.com to find out the public IP of the infected machine, and then run the nslookup process to connect to the network gandcrab.bit a.dnspod.com using the “.bit” top-level domain.
This version quickly spread in the cyberspace but its triumph was stopped at the end of February: a decryptor was created and placed online, thus letting victims decrypt their files without paying a ransom to the perpetrators.
GandCrab v2
The cybercriminals did not stay long with the answer: in a week, the GandCrab version 2 hit the users. It had a new encryption algorithm making the decryptor useless. The encrypted files had .CRAB extension and hardcoded domains changed to ransomware.bit and zonealarm.bit. This version was propagated via spam emails in March.
GandCrab v3
The next version came up in April with new ability to change a victim’s desktop wallpapers to a ransom note. Constant switching between desktop and the ransom banner was definitely aimed to exert more psychological pressure on the victims. Another new feature was RunOnce autorun registry key:
HKLMSOFTWAREMicrosoftWindowsCurrentVersionRunOncewhtsxydcvmtC:Documents and SettingsAdministratorApplication DataMicrosoftyrtbsc.exe
GandCrab v4
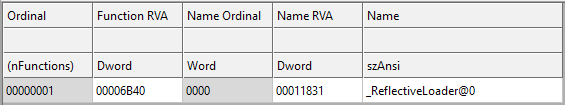
Finally, new, the fourth version of Gandcrab v4 has come up in July with a variety of significant updates, including a new encryption algorithm. As Comodo analyst discovered, the malware now uses Tiny Encryption Algorithm (TEA) to avoid detection — one of the fastest and efficient cryptographic algorithms developed by David Wheeler and Roger Needham on the symmetric encryption base.
Also, all encrypted files now have an extension .KRAB instead of CRAB.
In addition, the cybercriminals changed the way of the ransomware dissemination. Now it’s spread through fake software crack sites. Once a user downloads and runs such “stuffing” crack, the ransomware drops on the computer.
Here is an example of such fake software crack. Crack_Merging_Image_to_PDF.exe, in reality, is GandCrab v4.
Let’s see in details what will happen if a user runs this file.
Under the hood
As mentioned above, the GandCrab ransomware uses strong and fast TEA encryption algorithm to avoid detection. Decryption routine function gets the GandCrab plain file.
After the decryption is complete, the original GandCrab v4 file drops and runs, starting the killing raid.
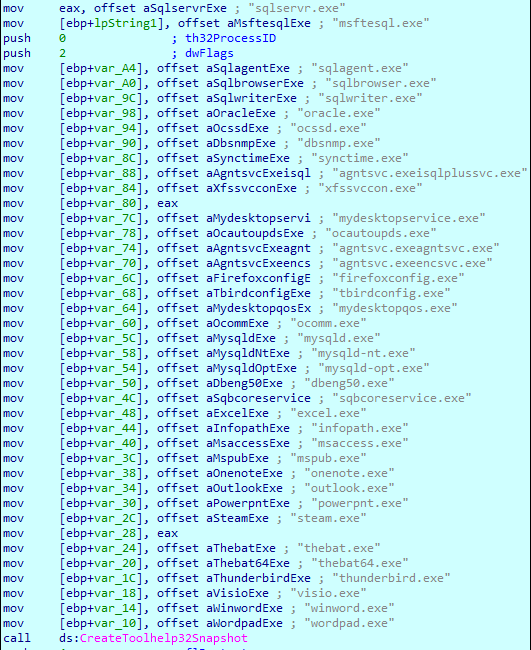
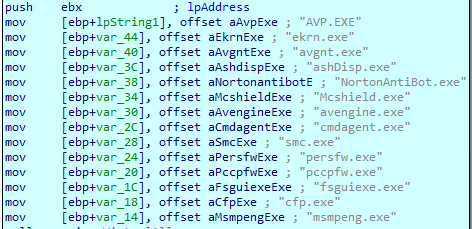
Firstly, the ransomware checks the list of the following processes with CreateToolhelp32Snapshot API and terminate any of them running:
Then ransomware checks for a keyboard layout. If it occurs to be Russian, GandCrab terminates the execution immediately.
Generating URL Process
Significantly, GandCrab uses a specific random algorithm to generate URL for each host. This algorithm are based on the following pattern:
http://{host}/{value1}/{value2}/{filename}.{extension}
The malware consistently creates all elements of the pattern, resulting in a unique URL.
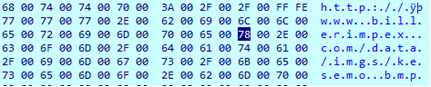
You can see the URL created by malware on in the right column.
Information Gathering
GandCrab collects the following information from the infected machine:
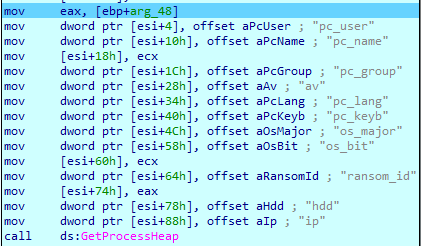
Then it checks for an antivirus running…
… and gathers the information about the system. After that, it encrypts all collected information with XOR and sends it to the Command-and-Control server. Significantly, it uses for encryption “jopochlen” key string that is an obscene language in Russian. That’s one more clear sign of Russian origination of the malware.
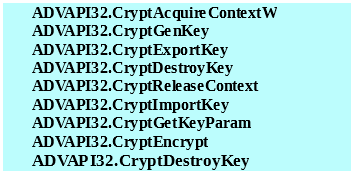
Key Generation
The ransomware generates private and public keys using Microsoft Cryptographic Provider and the following APIs:
Before starting the encryption process, the malware checks for some files…

… and folders to skip them during encryption:
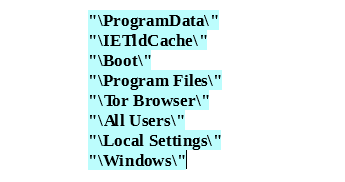
These files and folders are necessary for the ransomware to function properly. After that, GandCrab begins encrypting the victim’s files.
The ransom
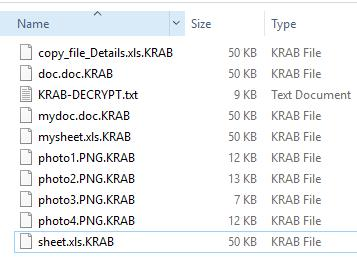
The ransom
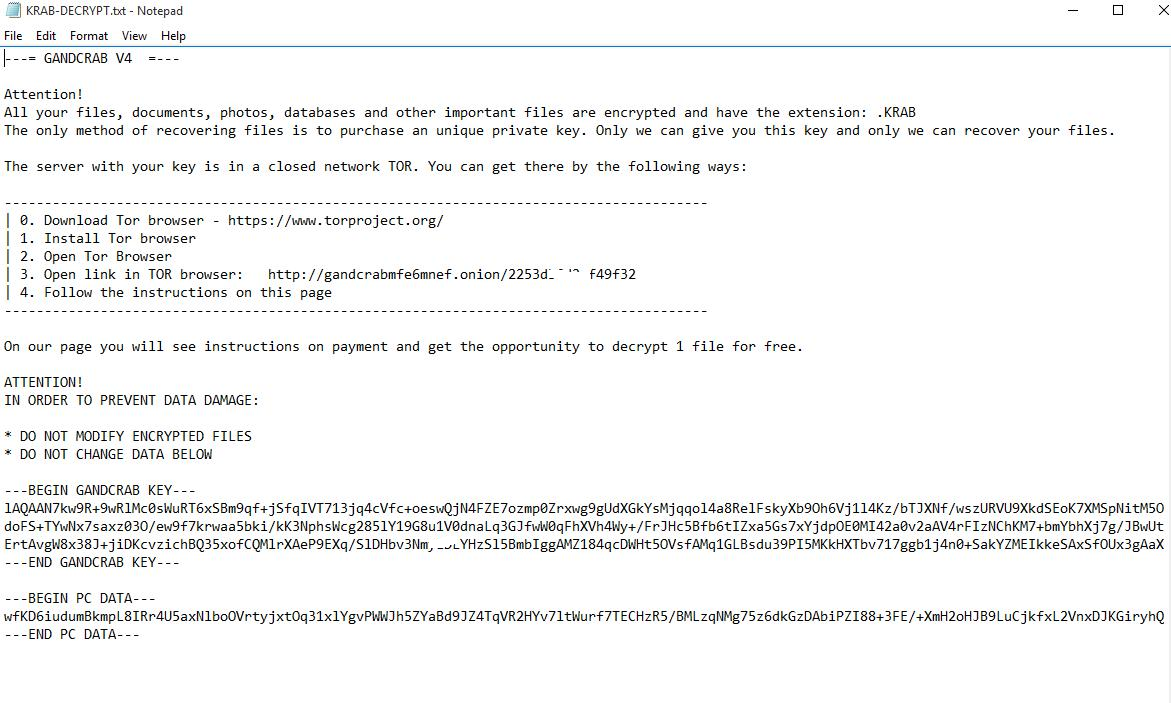
When the encryption is over, GandCrab opens a KRAB-DECRYPT.txt file that is the ransom note:
If the victim follows the perpetrators’ instructions and goes to their TOR site, she’ll find the ransom banner with the counter:
The payment page contents detailed instruction on how to pay the ransom.

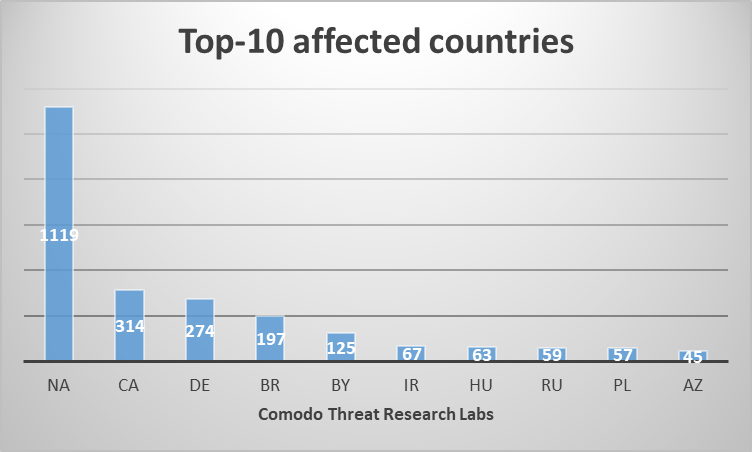
Comodo cybersecurity research team has traced the GandCrab communication IPs. Below is top-ten countries from this IPs list.

GandCrab hit users all over the world. Here is the list of top-ten countries affected by the malware.
“This finding of our analysts clearly demonstrate that malware swiftly changes and evolves in its rapidity of adaptation to cybersecurity vendors’ countermeasures”, comments Fatih Orhan, The Head of Comodo Threat Research Labs. “Obviously, we are at the edge of the time when all processes in the cybersecurity field are intensely catalyzing. Malware is quickly growing not only in quantity but also in its ability to mimic instantly. In Comodo Cybersecurity First Quarter 2018 Threat Report, we predicted that downsizing of ransomware was just a redeployment of forces and we’ll face with updated and more complicated samples in the nearest future. The appearance of GandCrab clearly confirms and demonstrate this trend. Thus, cybersecurity market should be ready to face with upcoming waves of attacks loaded with brand-new ransomware types.”
Live secure with Comodo!
Related Resources:
START FREE TRIAL GET YOUR INSTANT SECURITY SCORECARD FOR FREE
- SEO Powered Content & PR Distribution. Get Amplified Today.
- Platoblockchain. Web3 Metaverse Intelligence. Knowledge Amplified. Access Here.
- Source: https://blog.comodo.com/comodo-news/gandcrab-the-new-version-of-ransomware/
- 2018
- a
- ability
- About
- above
- added
- addition
- After
- algorithm
- algorithms
- All
- already
- analyst
- Analysts
- and
- Another
- answer
- antivirus
- api
- APIs
- April
- Attacks
- authors
- avoiding
- banner
- base
- based
- below
- between
- Bit
- Blog
- called
- change
- Changes
- changing
- check
- Checks
- clear
- clearly
- Column
- come
- comments
- Communication
- complete
- complicated
- computer
- Connect
- connection
- constant
- constantly
- contents
- Counter
- countries
- crack
- created
- creates
- cryptographic
- cybercriminals
- Cybersecurity
- cyberspace
- Dash
- David
- Decrypt
- deeper
- definitely
- demonstrate
- desktop
- detailed
- details
- detected
- Detection
- developed
- DID
- discovered
- distributed
- documents
- domain
- domains
- downloads
- Drops
- during
- each
- Edge
- efficient
- elements
- emails
- encrypted
- encryption
- enormous
- Environment
- Event
- everyone
- evolution
- example
- execution
- Exploit
- exploration
- extension
- Face
- fake
- FAST
- fastest
- Feature
- Features
- field
- File
- Files
- Find
- finding
- First
- following
- follows
- Forces
- Fourth
- Free
- Freshest
- from
- function
- future
- gathering
- generate
- generates
- generating
- generation
- get
- Go
- Goes
- good
- Growing
- happen
- head
- here
- Hit
- Hits
- host
- How
- How To
- HTTPS
- immediately
- in
- Including
- increasing
- information
- initial
- instant
- instead
- instructions
- IP
- IT
- itself
- January
- July
- Key
- keys
- King
- Labs
- language
- Last
- Layout
- letting
- List
- loader
- Long
- machine
- made
- Making
- malware
- March
- Market
- max-width
- mentioned
- Microsoft
- Modern
- more
- necessary
- network
- New
- New Features
- next
- ONE
- online
- opens
- original
- Other
- particular
- Pattern
- Pay
- paying
- payment
- PHP
- Plain
- plato
- Plato Data Intelligence
- PlatoData
- predicted
- pressure
- private
- process
- processes
- Products
- properly
- provider
- public
- public keys
- quantity
- Quarter
- quickly
- Race
- random
- Ransom
- ransomware
- React
- ready
- Reality
- registry
- representative
- research
- researchers
- Resources
- resulting
- Rid
- rig
- Run
- running
- russian
- Russians
- scorecard
- secure
- security
- should
- sign
- significant
- significantly
- site
- Sites
- So
- Software
- some
- something
- sophisticated
- spam
- specific
- speed
- spread
- Starting
- starts
- stay
- stopped
- strong
- such
- system
- Tea
- team
- The
- the information
- the world
- their
- thing
- threat
- Through
- throughout
- time
- to
- top-level
- top-level domain
- Tor
- Trend
- types
- unique
- upcoming
- updated
- Updates
- URL
- User
- users
- utilizes
- variety
- version
- via
- Victim
- victims
- Warriors
- waves
- week
- What
- will
- without
- world
- Your
- zephyrnet













