Reading Time: 4 minutes
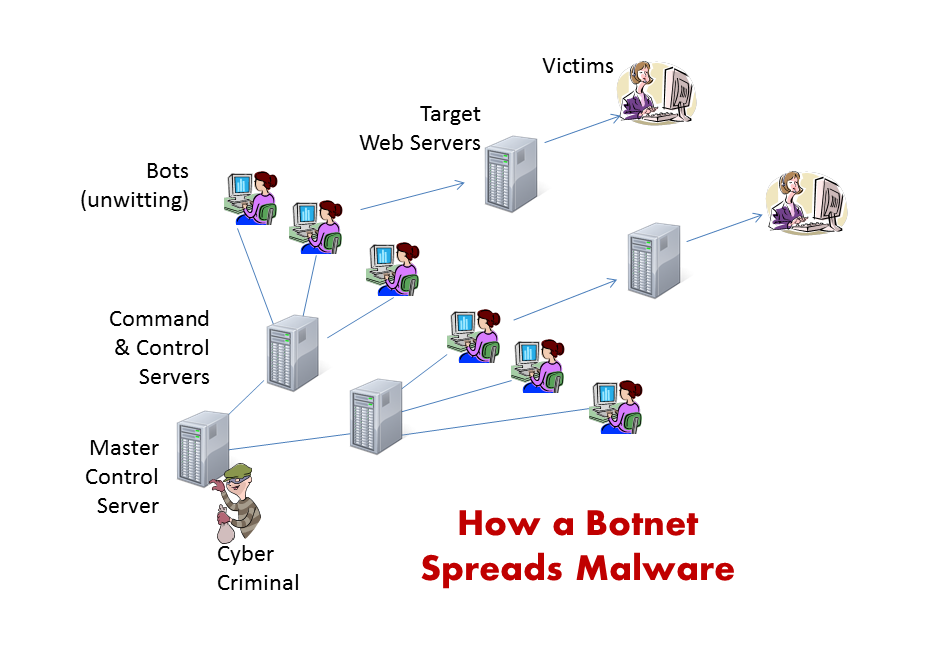
 On Monday, the US Department of Justice announced that law enforcement working in multiple countries had successfully seized control of the “Gameover Zeus” botnet that distributes the Zeus banking Trojan and a second botnet that distributes the Cryptolocker ransomware program. Zeus and its variants enable financial fraud by stealing login credentials and diverting financial transactions to the criminal’s accounts. Cyrptolocker blocks access to a user’s data files by encrypting them and will only allow access when the victim pays a ransome, usually $500.
On Monday, the US Department of Justice announced that law enforcement working in multiple countries had successfully seized control of the “Gameover Zeus” botnet that distributes the Zeus banking Trojan and a second botnet that distributes the Cryptolocker ransomware program. Zeus and its variants enable financial fraud by stealing login credentials and diverting financial transactions to the criminal’s accounts. Cyrptolocker blocks access to a user’s data files by encrypting them and will only allow access when the victim pays a ransome, usually $500.
It is believed that victims of these malware schemes have suffered losses cyber criminals in excess of $100 million dollars over the past 2 years!
A botnet is created by infecting a computer with malware that takes control of the victim’s computer so it can be used for the distribution of other malware, email spam or to launch denial of service attacks. The users of most botnet participants (bots) are not even aware their computers are being used for nefarious purposes.
The government’s actions give computer users a window of opportunity to rid their computers of botnet software and protect themselves from being victims in the future. Unfortunately, experts believe that the botnet creators will be able to reconnect their unwilling clients and distribute their malware again within 2 weeks or less.
If you want protect yourself from being part of a botnet or avoid being a victim of such cybercrime malware, Comodo security provides the most comprehensive protection possible. Whether you are using Comodo Internet Security (CIS) for the desktop user or Comodo Endpoint Security Management (CESM) system for the enterprise, Comodo’s Default/Deny strategy with Auto Sandboxing ensures that such malicious programs will never harm your system or your files.
Comodo security focuses on prevention, not purely detection. Comodo’s patent-pending Auto Sandboxing technology creates a real time, isolated environment that identifies safe, unsafe, and questionable files and executables and automatically isolates both unsafe and unknown files, allowing only known, trusted files to penetrate your system.
If a threat is known to be malicious, Comodo’s Antivirus (AV) will detect its signature and prevent any damage from occurring, i.e. the encryption of your files. If the threat is unknown, the HIPS and Auto-Sandbox will intercept the malware, stopping it in its tracks, as the virus is never actually installed on your system. Comodo AV labs detect blacklist signatures for malicious files such as CryptoLocker, so the ransomware would go straight into the Quarantine or Sandbox Management consoles of Comodo Endpoint Security Manager (CESM) where the admin could delete it.
CESM 3 packages unsurpassed protective power within our next-generation remote administrative console. This enables the administrator to receive real-time alerts through list or panoramic views of all endpoints and system management capabilities, a feature generally found only in dedicated Remote Monitoring and Management (RMM) systems. So, when the user opens the malicious message containing CryptoLocker, CES will detect the malicious (or unknown) file, automatically sandbox it, and alert the administrator. If the admin gets to the alert before Comodo labs, the administrator is able to remotely remove the ransomware from the end user’s computer, regardless of the end user’s location.
Four clicks to security:
- Administrator views the list of files within the sandbox.
- Administrator selects the malicious executable(s) to be removed.
- Administrator remotely accesses the end user’s computer to select the malicious file running on the sandbox.
- Administrator deletes the file location to rid the user’s system of the malicious application.
Four clicks to security. It’s really that simple! But don’t just take our word for it. Comodo Endpoint Security (CES) is powered by the same patent-pending prevention-based technology that our consumer product, Comodo Internet Security (CIS), uses to protect consumers against CryptoLocker. CIS was recently awarded the top position in the Proactive Security Challenge 64 by matousec.com, a project run by a respected group of independent security experts dedicated to improving end user security. Following the challenge, matousec.com named CIS the “Ultimate Protection Machine.”
In addition to its ability to protect enterprises from malware like CryptoLocker, ESM has many other great capabilities. For instance, the latest upgrade to ESM added several capabilities such as centralized monitoring of sandboxed (unknown) and malicious files, endpoint auto-synchronization via Active Directory, encrypted VNC sessions to local and remote endpoints, and support for Windows 7 Embedded Standard.
To become protected against botnets, Cryptolocker, Zeus and all their variants download a 60-Day, 60 user free trial now or contact cesmsales@comodo.com for the date of our next webinar.
START FREE TRIAL GET YOUR INSTANT SECURITY SCORECARD FOR FREE
- blockchain
- coingenius
- Comodo News
- cryptocurrency wallets
- cryptoexchange
- cyber security
- cybercriminals
- Cybersecurity
- CyberSecurity Comodo
- department of homeland security
- digital wallets
- firewall
- Kaspersky
- malware
- Mcafee
- NexBLOC
- plato
- plato ai
- Plato Data Intelligence
- Plato Game
- PlatoData
- platogaming
- VPN
- website security
- zephyrnet













