A new ransomware called CoronaVirus has been distributed through a fake web site pretending to promote the system optimization software and utilities from WiseCleaner.
With the increasing fears and anxiety of the Coronavirus (COVID-19) outbreak, an attacker has started to build a campaign to distribute a malware cocktail consisting of the CoronaVirus Ransomware and the Kpot information-stealing Trojan.
This new ransomware was discovered by MalwareHunterTeam and after further digging into the source of the file, we have been able to determine how the threat actor plans on distributing the ransomware and possible clues suggesting that it may actually be a wiper.
CoronaVirus Ransomware spread through fake WiseCleaner site
To distribute the malware, the attackers have created a web site that impersonates the legitimate Windows system utility site WiseCleaner.com.
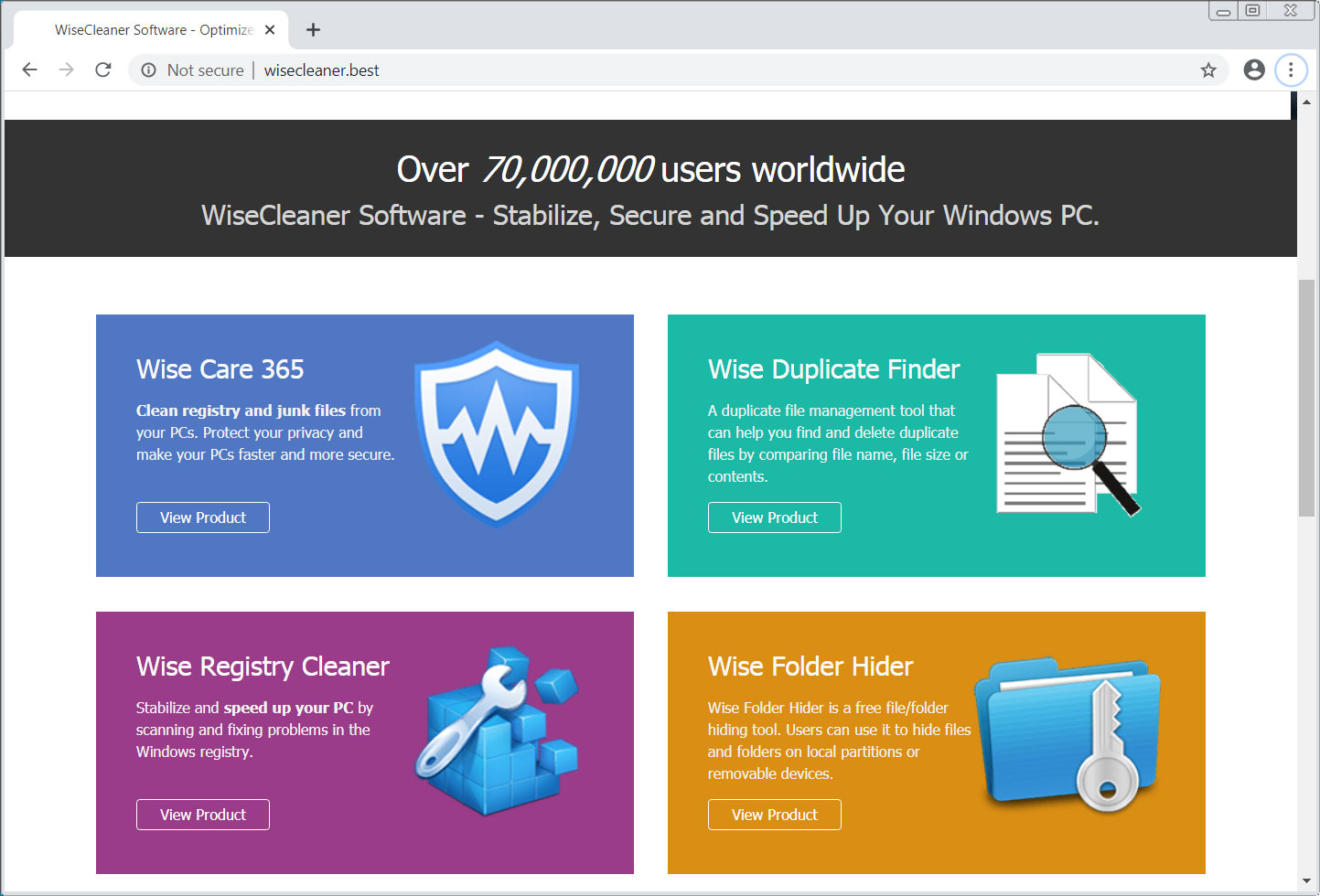
The downloads on this site are not active but have distributed a file called WSHSetup.exe that currently acts as a downloader for both the CoronaVirus Ransomware and a password-stealing Trojan called Kpot.
When the program is executed, it will attempt to download a variety of files from a remote web site. Currently, only the file1.exe and file2.exe are available for download, but you can see that it attempts to download a total of seven files.
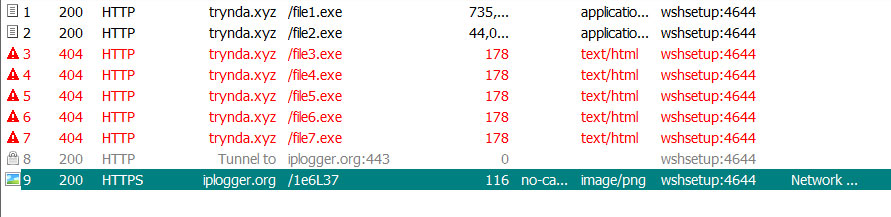
The first file downloaded by the installer is 'file1.exe' and is the Kpot password-stealing Trojan.
When executed, it will attempt to steal cookies and login credentials from web browsers, messaging programs, VPNs, FTP, email accounts, gaming accounts such as Steam and Battle.net, and other services. The malware will also take a screenshot of the active desktop and attempt to steal cryptocurrency wallets stored on the infected computer.
This information is then uploaded to a remote site operated by the attackers.
The second file, file2.exe, is the CoronaVirus Ransomware, which will be used to encrypt the files on the computer.
When encrypting files, it will only target files that contain the following extensions:
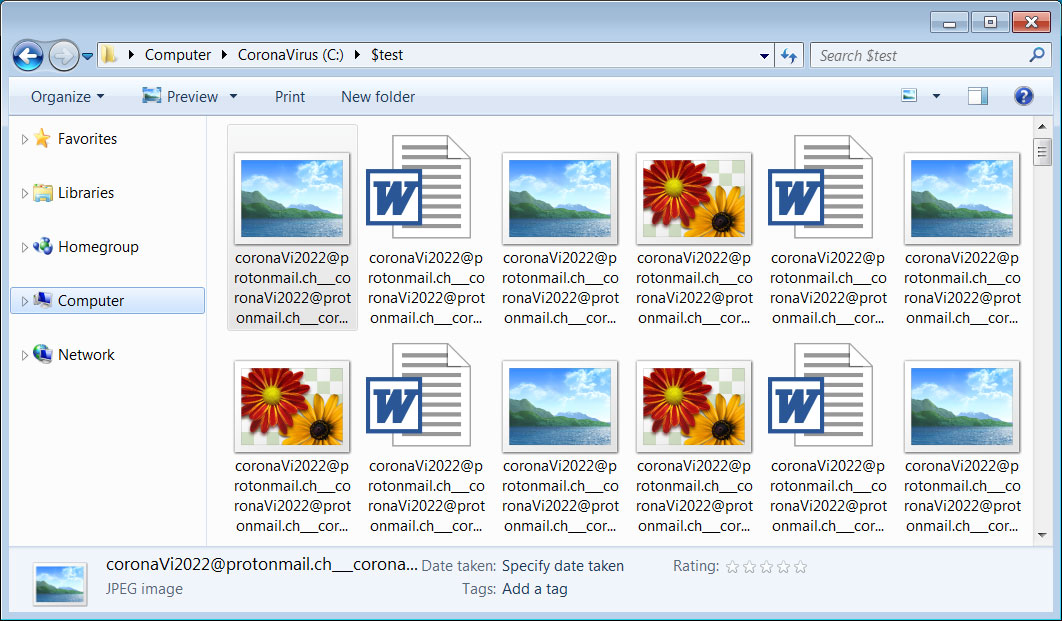
.bak, .bat, .doc, .jpg, .jpe, .txt, .tex, .dbf, .xls, .cry, .xml, .vsd, .pdf, .csv, .bmp, .tif, .tax, .gif, .gbr, .png, .mdb, .mdf, .sdf, .dwg, .dxf, .dgn, .stl, .gho, .ppt, .acc, .vpd, .odt, .ods, .rar, .zip, .cpp, .pas, .asm, .rtf, .lic, .avi, .mov, .vbs, .erf, .epf, .mxl, .cfu, .mht, .bak, .oldFiles that are encrypted will be renamed so that it continues to use the same extension, but the file name will be changed to the attacker's email address. For example, test.jpg would be encrypted and renamed to 'coronaVi2022@protonmail.ch___1.jpg'.
In some cases, like below, it may prepend the email address multiple times to the file name.
In each folder that is encrypted and on the desktop, a ransom note named CoronaVirus.txt will be created that demands 0.008 (~$50) bitcoins to a hardcoded bitcoin address of bc1qkk6nwhsxvtp2akunhkke3tjcy2wv2zkk00xa3j, which has not received any payments as of yet.
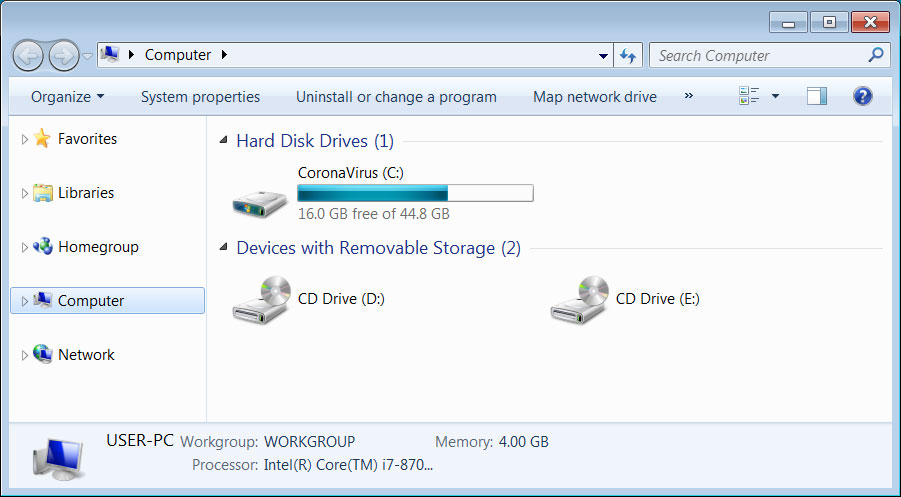
The ransomware will also rename the C: drive to CoronaVirus as shown below, which adds nothing other than the attacker trolling the victims.
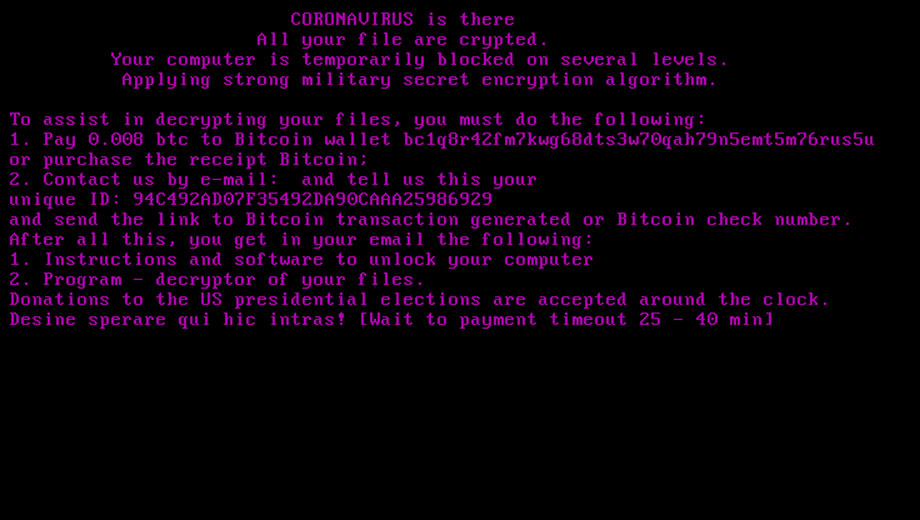
On reboot, the ransomware will display a lock screen displaying the same text from the ransom note before Windows is loaded as seen below.
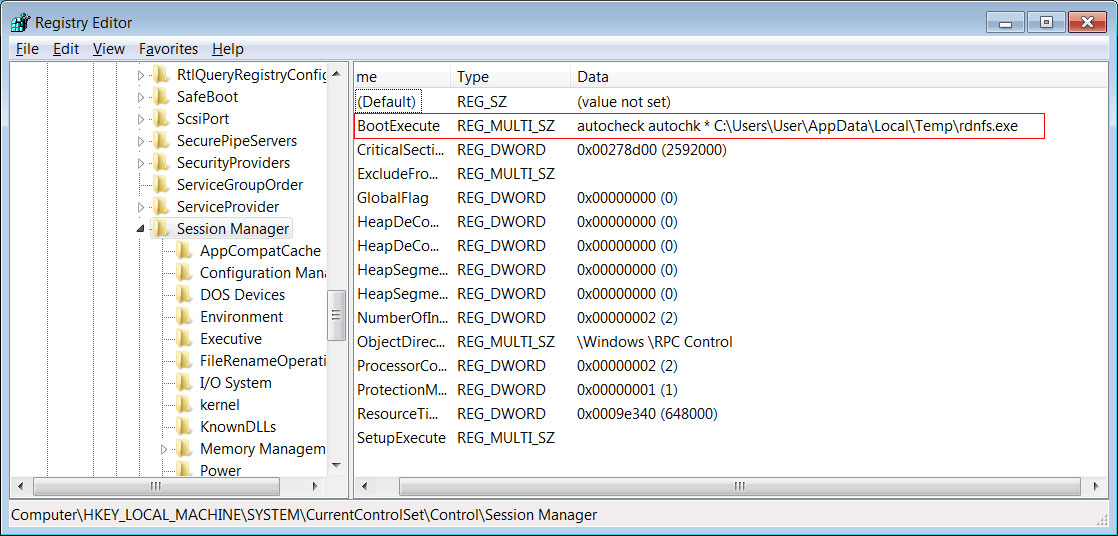
Head of SentinelLabs Vitali Kremez told BleepingComputer that this is being displayed through a modification of the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager "BootExecute" Registry value that launches an executable from the %Temp% folder before loading any Windows services on boot.
After 45 minutes, the lock screen will switch to a slightly different message. You are still unable to enter any code, though, to get back into the system.
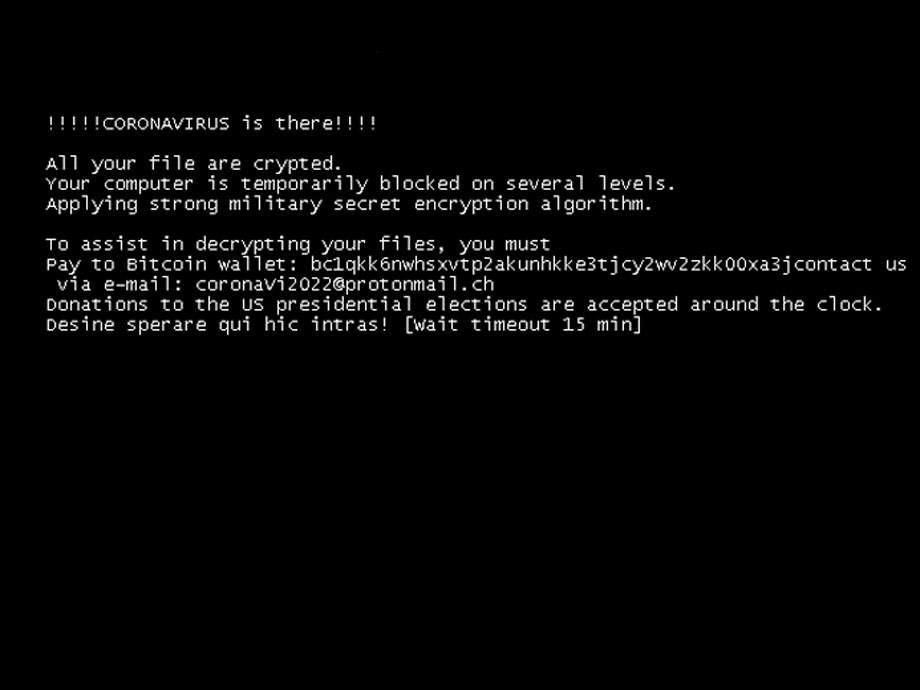
After 15 minutes, it boots back into Windows and upon login will display the CoronaVirus.txt ransom note.
This is a strange ransomware and is still being analyzed for weaknesses.
Based on the low ransom amount, static bitcoin address, and political message, it is strongly suspected that this ransomware is being used more as a cover for the Kpot infection rather than to generate actual ransom payments.
"Donations to the US presidential elections are accepted around the clock."
BleepingComputer's theory is that the ransomware component is being used to distract the user from realizing that the Kpot information-stealing Trojan was also installed to steal passwords, cookies, and cryptocurrency wallets.
Anyone who has been infected with this attack should immediately use another computer to change all of their online passwords as they have now been compromised by the Kpot info-stealer.
IOCs
Hashes:
Installer: 5987a6e42c3412086b7c9067dc25f1aaa659b2b123581899e9df92cb7907a3ed
Ransomware: 3299f07bc0711b3587fe8a1c6bf3ee6bcbc14cb775f64b28a61d72ebcb8968d3
Kpot: a08db3b44c713a96fe07e0bfc440ca9cf2e3d152a5d13a70d6102c15004c4240Associated Files:
CoronaVirus.txtAssociated emails:
coronaVi2022@protonmail.chRansom Note text:
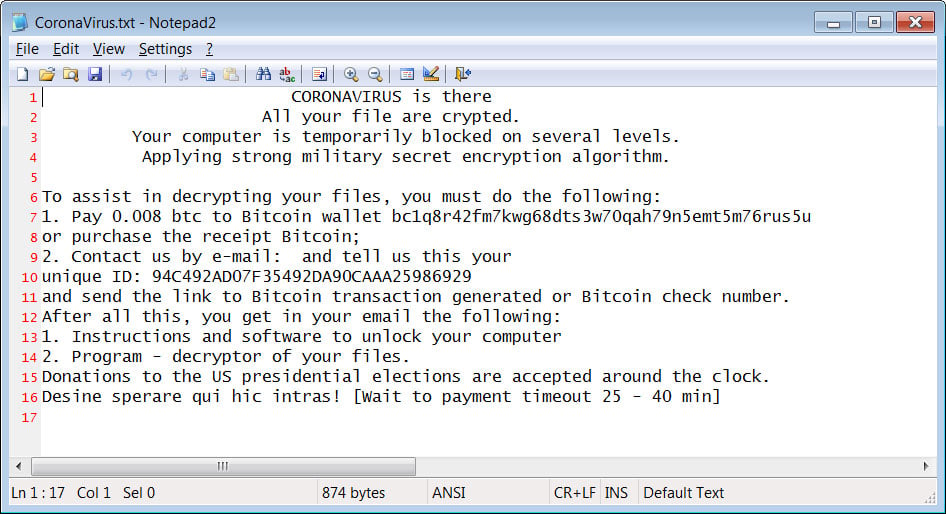
CORONAVIRUS is there
All your file are crypted.
Your computer is temporarily blocked on several levels.
Applying strong military secret encryption algorithm.
To assist in decrypting your files, you must do the following:
1. Pay 0.008 btc to Bitcoin wallet bc1q8r42fm7kwg68dts3w70qah79n5emt5m76rus5u
or purchase the receipt Bitcoin;
2. Contact us by e-mail: and tell us this your
unique ID: 94C492AD07F35492DA90CAAA25986929
and send the link to Bitcoin transaction generated or Bitcoin check number.
After all this, you get in your email the following:
1. Instructions and software to unlock your computer
2. Program - decryptor of your files.
Donations to the US presidential elections are accepted around the clock.
Desine sperare qui hic intras! [Wait to payment timeout 25 - 40 min]


Comments
Engineer_AI - 1 year ago
Ransomware is the worst! You either are forced to pay to the hacker, or to the IT guy (who ends up charging almost as much). Ransomware attacks have risen, as folks have managed to engineer AI hacking bots, which hold public files hostage, containing important information. My point is that a surge in these attacks is letting us know that those who engineer AI hacking bots, are rarely ever booked, irrespective of country.
State Sponsored hackers have begun engineering AI to capitalize on this pandemic. I cannot believe how lax the Infosec dept of any country can get, as malicious actors engineer AI bots and gain access to personal, and at time, confidential data. The game has risen so much that they've begun to engineer AI hacking software to get into the government's pants (DNC hack of 2016). Appalling!
R-K - 1 year ago
Just support death penalties against those international ransomware cyberterrorists.