 Reading Time: 3 minutes
Reading Time: 3 minutes
What’s worse, having your network compromised by a hacker or having your network compromised by a hacker and not knowing about it?
Advanced Persistent Threats and zero-day attacks can go unnoticed for days and weeks, even on the networks of companies that have heavily invested in security software, posing a catastrophic threat to sensitive employee data and business-critical information systems.
Today’s network administrators face the unenviable task of making sure employees are kept secure against an ever-rising tide of malware, hacking attacks, social engineering and phishing. It’s an unpredictable and poisonous environment which confronts even the best prepared administrators with a unique challenge on a daily basis.
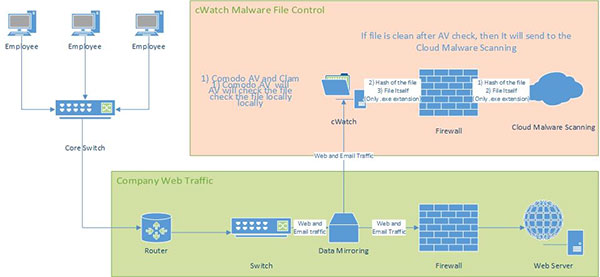
Comodo cWatch meets this challenge by providing immediate notification and visibility over malware outbreaks over all network and mail traffic. After the application has been installed and configured on a local server, cWatch uses a proprietary combination of cloud and local based virus scans, real-time behavior analysis, automatic file look-up and multiple blacklist checks to quickly and accurately identify known and unknown threats.
Once configured, all network traffic will be examined by the following cWatch technologies:
Cloud-based file look-up service – File reputation service which Instantly checks a files signature against the very latest database to ascertain whether or not it is trusted, malicious or unknown.
Comodo Automated Malware Analysis (CAMAS) –A cloud based behavior analysis service which improves detection of zero-day threats by rigorously testing the run-time actions of unknown files
ClamAV – ClamAV is designed to scan mail gateways for malicious files and provides another layer of protection on top of Comodo Antivirus
Blacklist checking – Real-time checks of whether the domains, URLs and IP addresses visited by your users are flagged as malicious by major blacklisting services.
cWatch is an innovative, fully-optimized solution which delivers near-instant analysis of traffic with no loss of network speed to end users. cWatch analyses a mirror of network traffic and leverages constantly updated cloud-based monitoring technologies which use a fraction of the resources and bandwidth of traditional, host-based scanners.
Suppose an Employee connects to a webpage and attempts to download an executable
- cWatch downloads the executable to the cWatch server and runs real-time a real time check on our File Lookup Server (FLS) to ascertain the file’s trustworthiness.
- If the file in on the whitelist (known good), the download is allowed to continue
- If the file is on the blacklist (known bad), the user is shown a warning and the download is blocked
- If the file is unknown then cWatch wraps the executable with our containment technology and delivers that modified version to the end-user
From this point, The executable will run on the endpoint inside its own container/sandbox. It will run in an isolated environment from which it cannot modify other processes running on the endpoint nor access user data. This ensures the download is secure because it is not possible for the file to infect the endpoint, even if it transpires to be malicious.
Simultaneously, the file will be uploaded to Comodo labs where it will undergo and series of automated and manual tests. These include virus scans, behavioural analysis, heuristic analysis and manual inspection.
For more information contact Comodo at enterprisesolutions@comodo.com
Related Resources:
Zero Trust
What is Zero Day Malware?
Malware Analysis
START FREE TRIAL GET YOUR INSTANT SECURITY SCORECARD FOR FREE
- SEO Powered Content & PR Distribution. Get Amplified Today.
- PlatoAiStream. Web3 Data Intelligence. Knowledge Amplified. Access Here.
- Minting the Future w Adryenn Ashley. Access Here.
- Buy and Sell Shares in PRE-IPO Companies with PREIPO®. Access Here.
- Source: https://blog.comodo.com/it-security/cwatch-delivers-umatched-awareness-zero-day-threats-malware/
- :has
- :is
- :not
- :where
- a
- About
- about IT
- access
- accurately
- actions
- addresses
- administrators
- After
- against
- All
- an
- Analyses
- analysis
- and
- Another
- Application
- ARE
- AS
- At
- Attacks
- Attempts
- Automated
- Automatic
- awareness
- Bad
- Bandwidth
- based
- basis
- BE
- because
- been
- BEST
- Blog
- by
- CAN
- cannot
- catastrophic
- challenge
- check
- Checks
- click
- Cloud
- combination
- Comodo News
- Companies
- Compromised
- connects
- constantly
- Containment
- continuously
- daily
- data
- Database
- day
- Days
- delivers
- dependable
- designed
- Detection
- domains
- download
- downloads
- Employee
- employees
- end
- Endpoint
- Engineering
- ensures
- Environment
- Even
- Event
- Face
- File
- Files
- flagged
- following
- For
- fraction
- Free
- from
- get
- Go
- good
- hacker
- hacking
- Have
- having
- heavily
- http
- HTTPS
- identify
- if
- immediate
- in
- include
- information
- Information Systems
- innovative
- installed
- instant
- instantly
- Internet
- Internet Security
- invested
- IP
- IP addresses
- isolated
- IT
- ITS
- jpg
- kept
- Knowing
- known
- Labs
- latest
- layer
- leverages
- local
- lookup
- loss
- major
- Making
- malware
- manual
- Meets
- mirror
- modified
- modify
- monitoring
- more
- multiple
- network
- network traffic
- networks
- news
- no
- notification
- of
- on
- or
- Other
- our
- over
- own
- phishing
- PHP
- plato
- Plato Data Intelligence
- PlatoData
- Point
- possible
- prepared
- processes
- proprietary
- protection
- provides
- providing
- quickly
- real
- real-time
- reputation
- Resources
- Run
- running
- scan
- scorecard
- secure
- security
- send
- sensitive
- Series
- service
- Services
- shown
- Social
- Social Engineering
- Software
- solution
- Solutions
- speed
- Systems
- Task
- Technologies
- Technology
- Testing
- tests
- Thanksgiving
- that
- The
- then
- These
- this
- threat
- threats
- Tide
- time
- to
- top
- traditional
- traffic
- trusted
- unique
- unknown
- unpredictable
- updated
- uploaded
- use
- User
- users
- uses
- version
- very
- visibility
- visited
- warning
- Weeks
- whether
- which
- whitelist
- will
- with
- worse
- Your
- zephyrnet
- zero
- Zero Day












