It’s all about the data.
One thing is clear: the business value of data continues to grow, making it a bank’s primary piece of intellectual property.
From a cyber risk perspective, attacks on data are the most prominent threat to banks.
Regulators, cyber insurance firms and auditors are paying much closer attention to the integrity, resilience and recoverability of banks’ data — as well as the IT infrastructure and systems that store the data.
So, what does this mean for the security of enterprise storage and backup systems?
Just a few years ago, almost no banking chief information security officer (CISO) thought that storage and backups were important. That’s no longer the case today.
Ransomware has pushed backup and recovery back onto the IT and corporate agenda.
Ransomware groups such as Conti, Hive and REvil are actively targeting enterprise storage and backup systems to prevent banks from recovering their data.
These attackers realize that an attack on storage or backup systems is the single biggest determining factor to show if the bank will pay the ransom. This has forced banks to look again at potential holes in their safety nets by reviewing their storage, backup and data recovery strategies.
Storage and backup security in financial services
Continuity published a research report at the end of last year in which we surveyed 200 infosec leaders within the banking and financial services sector. One of the most alarming findings was that almost 60% of respondents are not confident in their ability to recover from a ransomware attack.
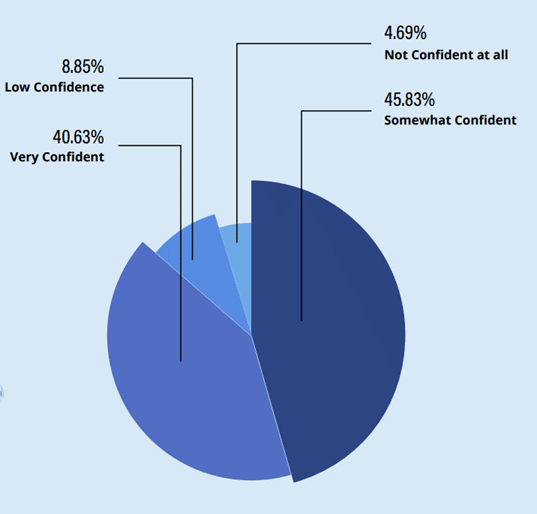
There’s clearly a recognition that as an industry, we have security blind spots.
Without a sound storage, backup and recovery strategy, companies have little chance of surviving a ransomware attack, even if they do end up paying the ransom.
The banking sector is one of the most heavily regulated industries. Audits are performed both internally and externally and tend to evolve year over year based on advances in technology, industry regulation changes and shifts in the threat landscape.
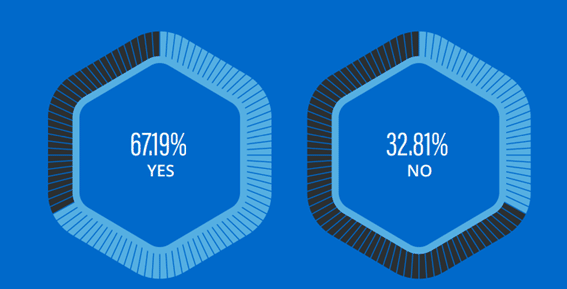
It was interesting to learn how pervasive storage and backup security controls have become, as part of IT auditing. In fact, more than two-thirds of respondents identified securing storage and backup being specifically addressed in recent external audits.
Summary and recommendations
Considering storage and backup compromise are at the heart of all current ransomware kits, surely the time has come for us to boost our knowledge — as well as our strategies — in protecting and hardening our storage and backup systems.
While immutability is helpful in remediating cyberthreats, it is only the beginning of a comprehensive cyber resiliency strategy.
According to the analyst firm Gartner:
“Harden the components of enterprise backup and recovery infrastructure against attacks by routinely examining backup application, storage and network access and comparing this against expected or baseline activity.”
You wouldn’t dream of not continuously scanning your endpoints, OS and network layers for security risks. So why wouldn’t you do it for your most important layer of IT?
This is why I recommend deploying a vulnerability management solution to help you continuously scan your storage and backup systems to automatically detect security misconfigurations and vulnerabilities.
These solutions also prioritize risks in order of urgency and business impact, and some of them even include remediation guidance and auto-remediation features.
The 5 key opportunities for improvement include:
- Assign higher priority to improving the security of enterprise storage and backup systems;
- Build up knowledge and skill sets — and improve collaboration between your Infosec and IT infrastructure teams;
- Define comprehensive security baselines for all components of storage and backup systems
- Use automation to reduce exposure to risk, and allow much more agility in adapting to changing priorities. Vulnerability management solutions can go a long way to helping you reduce this exposure; and
- Apply much stricter controls and more comprehensive testing of storage security and the ability to recover from an attack. This will not only improve confidence but will also help identify key data assets that might not meet the required level of data protection.
Doron Pinhas is chief technology officer at Continuity and co-author of the NIST special publication, “Security Guidelines for Storage Infrastructure.” He has more than 20 years’ experience in data and storage management, mission critical computing, operating system design and development, cloud computing and networking architecture.
- ant financial
- Bankinnovation
- blockchain
- blockchain conference fintech
- chime fintech
- coinbase
- coingenius
- crypto conference fintech
- Cybersecurity
- fintech
- fintech app
- fintech innovation
- OpenSea
- PayPal
- paytech
- payway
- plato
- plato ai
- Plato Data Intelligence
- PlatoData
- platogaming
- ransomware
- razorpay
- Revolut
- Ripple
- Risk & Security
- square fintech
- stripe
- tencent fintech
- xero
- zephyrnet













