1Department of Applied Physics, Graduate School of Engineering, The University of Tokyo, 7-3-1 Hongo, Bunkyo-ku, Tokyo 113-8656, Japan
2Centre for Quantum Computation & Communication Technology, School of Science, RMIT University, Melbourne VIC 3000, Australia
3Department of Physics, Faculty of Science, Kyushu University, 744 Motooka, Nishi-ku, Fukuoka, Japan
4Photon Science Center, Graduate School of Engineering, The University of Tokyo, 7-3-1 Hongo, Bunkyo-ku, Tokyo 113-8656, Japan
Find this paper interesting or want to discuss? Scite or leave a comment on SciRate.
Abstract
Recent studies showed the finite-size security of binary-modulation CV-QKD protocols against general attacks. However, they gave poor key-rate scaling against transmission distance. Here, we extend the security proof based on complementarity, which is used in the discrete-variable QKD, to the previously developed binary-modulation CV-QKD protocols with the reverse reconciliation under the finite-size regime and obtain large improvements in the key rates. Notably, the key rate in the asymptotic limit scales linearly against the attenuation rate, which is known to be optimal scaling but is not achieved in previous finite-size analyses. This refined security approach may offer full-fledged security proofs for other discrete-modulation CV-QKD protocols.
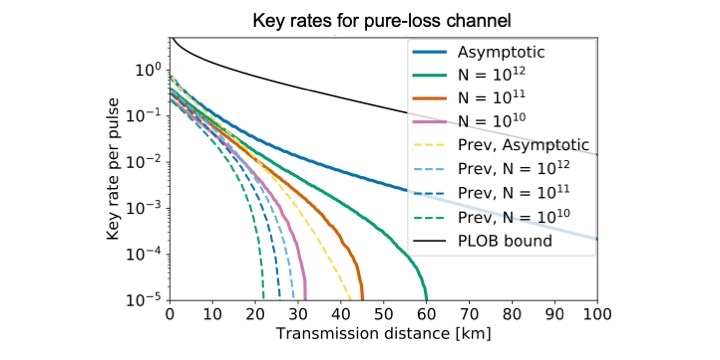
Featured image: Key rates obtained by our new results (solid lines), previous results (broken lines), and the ultimate limit of one-way QKDs (thin black line). The attenuation rate of the channel is assumed to be ${10^{-0.02L}}$ for the transmission distance L [km]. The asymptotic key rate of our new result is in parallel with the ultimate limit.
Popular summary
► BibTeX data
► References
[1] Charles H. Bennett and Gilles Brassard. “Quantum cryptography: Public key distribution and coin tossing”. Theoretical Computer Science 560, 7–11 (2014).
https://doi.org/10.1016/j.tcs.2014.05.025
[2] C. E. Shannon. “Communication theory of secrecy systems”. The Bell System Technical Journal 28, 656–715 (1949).
https://doi.org/10.1002/j.1538-7305.1949.tb00928.x
[3] T. C. Ralph. “Continuous variable quantum cryptography”. Phys. Rev. A 61, 010303 (1999).
https://doi.org/10.1103/PhysRevA.61.010303
[4] Mark Hillery. “Quantum cryptography with squeezed states”. Phys. Rev. A 61, 022309 (2000).
https://doi.org/10.1103/PhysRevA.61.022309
[5] Daniel Gottesman and John Preskill. “Secure quantum key distribution using squeezed states”. Phys. Rev. A 63, 022309 (2001).
https://doi.org/10.1103/PhysRevA.63.022309
[6] N. J. Cerf, M. Lévy, and G. Van Assche. “Quantum distribution of Gaussian keys using squeezed states”. Phys. Rev. A 63, 052311 (2001).
https://doi.org/10.1103/PhysRevA.63.052311
[7] Frédéric Grosshans and Philippe Grangier. “Continuous Variable Quantum Cryptography Using Coherent States”. Phys. Rev. Lett. 88, 057902 (2002).
https://doi.org/10.1103/PhysRevLett.88.057902
[8] Frédéric Grosshans, Gilles Van Assche, Jérôme Wenger, Rosa Brouri, Nicolas J. Cerf, and Philippe Grangier. “Quantum key distribution using gaussian-modulated coherent states”. Nature 421, 238–241 (2003).
https://doi.org/10.1038/nature01289
[9] Christian Weedbrook, Andrew M. Lance, Warwick P. Bowen, Thomas Symul, Timothy C. Ralph, and Ping Koy Lam. “Quantum Cryptography Without Switching”. Phys. Rev. Lett. 93, 170504 (2004).
https://doi.org/10.1103/PhysRevLett.93.170504
[10] Ch. Silberhorn, T. C. Ralph, N. Lütkenhaus, and G. Leuchs. “Continuous Variable Quantum Cryptography: Beating the 3 dB Loss Limit”. Phys. Rev. Lett. 89, 167901 (2002).
https://doi.org/10.1103/PhysRevLett.89.167901
[11] Yi-Bo Zhao, Matthias Heid, Johannes Rigas, and Norbert Lütkenhaus. “Asymptotic security of binary modulated continuous-variable quantum key distribution under collective attacks”. Phys. Rev. A 79, 012307 (2009).
https://doi.org/10.1103/PhysRevA.79.012307
[12] Raúl García-Patrón and Nicolas J. Cerf. “Continuous-Variable Quantum Key Distribution Protocols Over Noisy Channels”. Phys. Rev. Lett. 102, 130501 (2009).
https://doi.org/10.1103/PhysRevLett.102.130501
[13] Anthony Leverrier and Philippe Grangier. “Unconditional Security Proof of Long-Distance Continuous-Variable Quantum Key Distribution with Discrete Modulation”. Phys. Rev. Lett. 102, 180504 (2009).
https://doi.org/10.1103/PhysRevLett.102.180504
[14] Anthony Leverrier and Philippe Grangier. “Erratum: Unconditional Security Proof of Long-Distance Continuous-Variable Quantum Key Distribution with Discrete Modulation [Phys. Rev. Lett. 102, 180504 (2009)]”. Phys. Rev. Lett. 106, 259902 (2011).
https://doi.org/10.1103/PhysRevLett.106.259902
[15] Eneet Kaur, Saikat Guha, and Mark M. Wilde. “Asymptotic security of discrete-modulation protocols for continuous-variable quantum key distribution”. Phys. Rev. A 103, 012412 (2021).
https://doi.org/10.1103/PhysRevA.103.012412
[16] Shouvik Ghorai, Philippe Grangier, Eleni Diamanti, and Anthony Leverrier. “Asymptotic Security of Continuous-Variable Quantum Key Distribution with a Discrete Modulation”. Phys. Rev. X 9, 021059 (2019).
https://doi.org/10.1103/PhysRevX.9.021059
[17] Jie Lin, Twesh Upadhyaya, and Norbert Lütkenhaus. “Asymptotic Security Analysis of Discrete-Modulated Continuous-Variable Quantum Key Distribution”. Phys. Rev. X 9, 041064 (2019).
https://doi.org/10.1103/PhysRevX.9.041064
[18] Wen-Bo Liu, Chen-Long Li, Yuan-Mei Xie, Chen-Xun Weng, Jie Gu, Xiao-Yu Cao, Yu-Shuo Lu, Bing-Hong Li, Hua-Lei Yin, and Zeng-Bing Chen. “Homodyne Detection Quadrature Phase Shift Keying Continuous-Variable Quantum key Distribution with High Excess Noise Tolerance”. PRX Quantum 2, 040334 (2021).
https://doi.org/10.1103/PRXQuantum.2.040334
[19] Twesh Upadhyaya, Thomas van Himbeeck, Jie Lin, and Norbert Lütkenhaus. “Dimension Reduction in Quantum Key Distribution for Continuous- and Discrete-Variable Protocols”. PRX Quantum 2, 020325 (2021).
https://doi.org/10.1103/PRXQuantum.2.020325
[20] Aurélie Denys, Peter Brown, and Anthony Leverrier. “Explicit asymptotic secret key rate of continuous-variable quantum key distribution with an arbitrary modulation”. Quantum 5, 540 (2021).
https://doi.org/10.22331/q-2021-09-13-540
[21] Anthony Leverrier, Frédéric Grosshans, and Philippe Grangier. “Finite-size analysis of a continuous-variable quantum key distribution”. Phys. Rev. A 81, 062343 (2010).
https://doi.org/10.1103/PhysRevA.81.062343
[22] Anthony Leverrier. “Composable Security Proof for Continuous-Variable Quantum Key Distribution with Coherent States”. Phys. Rev. Lett. 114, 070501 (2015).
https://doi.org/10.1103/PhysRevLett.114.070501
[23] E. Samsonov, R. Goncharov, A. Gaidash, A. Kozubov, V. Egorov, and A. Gleim. “Subcarrier wave continuous variable quantum key distribution with discrete modulation: mathematical model and finite-key analysis”. Scientific Reports 10, 10034 (2020).
https://doi.org/10.1038/s41598-020-66948-0
[24] Panagiotis Papanastasiou and Stefano Pirandola. “Continuous-variable quantum cryptography with discrete alphabets: Composable security under collective Gaussian attacks”. Phys. Rev. Research 3, 013047 (2021).
https://doi.org/10.1103/PhysRevResearch.3.013047
[25] Panagiotis Papanastasiou, Carlo Ottaviani, and Stefano Pirandola. “Security of continuous-variable quantum key distribution against canonical attacks”. In 2021 International Conference on Computer Communications and Networks (ICCCN). Pages 1–6. (2021).
https://doi.org/10.1109/ICCCN52240.2021.9522349
[26] Alexander G. Mountogiannakis, Panagiotis Papanastasiou, Boris Braverman, and Stefano Pirandola. “Composably secure data processing for Gaussian-modulated continuous-variable quantum key distribution”. Phys. Rev. Research 4, 013099 (2022).
https://doi.org/10.1103/PhysRevResearch.4.013099
[27] Florian Kanitschar, Ian George, Jie Lin, Twesh Upadhyaya, and Norbert Lütkenhaus. “Finite-Size Security for Discrete-Modulated Continuous-Variable Quantum Key Distribution Protocols” (2023). arXiv:2301.08686.
arXiv:2301.08686
[28] F. Furrer, T. Franz, M. Berta, A. Leverrier, V. B. Scholz, M. Tomamichel, and R. F. Werner. “Continuous Variable Quantum Key Distribution: Finite-Key Analysis of Composable Security against Coherent Attacks”. Phys. Rev. Lett. 109, 100502 (2012).
https://doi.org/10.1103/PhysRevLett.109.100502
[29] F. Furrer, T. Franz, M. Berta, A. Leverrier, V. B. Scholz, M. Tomamichel, and R. F. Werner. “Erratum: Continuous Variable Quantum Key Distribution: Finite-Key Analysis of Composable Security Against Coherent Attacks [Phys. Rev. Lett. 109, 100502 (2012)]”. Phys. Rev. Lett. 112, 019902 (2014).
https://doi.org/10.1103/PhysRevLett.112.019902
[30] Fabian Furrer. “Reverse-reconciliation continuous-variable quantum key distribution based on the uncertainty principle”. Phys. Rev. A 90, 042325 (2014).
https://doi.org/10.1103/PhysRevA.90.042325
[31] Mario Berta, Fabian Furrer, and Volkher B. Scholz. “The smooth entropy formalism for von Neumann algebras”. Journal of Mathematical Physics 57, 015213 (2016).
https://doi.org/10.1063/1.4936405
[32] Anthony Leverrier, Raúl García-Patrón, Renato Renner, and Nicolas J. Cerf. “Security of Continuous-Variable Quantum Key Distribution Against General Attacks”. Phys. Rev. Lett. 110, 030502 (2013).
https://doi.org/10.1103/PhysRevLett.110.030502
[33] Anthony Leverrier. “Security of Continuous-Variable Quantum Key Distribution via a Gaussian de Finetti Reduction”. Phys. Rev. Lett. 118, 200501 (2017).
https://doi.org/10.1103/PhysRevLett.118.200501
[34] A Leverrier, E Karpov, P Grangier, and N J Cerf. “Security of continuous-variable quantum key distribution: towards a de Finetti theorem for rotation symmetry in phase space”. New Journal of Physics 11, 115009 (2009).
https://doi.org/10.1088/1367-2630/11/11/115009
[35] Anthony Leverrier. “SU(p,q) coherent states and a Gaussian de Finetti theorem”. Journal of Mathematical Physics 59, 042202 (2018).
https://doi.org/10.1063/1.5007334
[36] Cosmo Lupo, Carlo Ottaviani, Panagiotis Papanastasiou, and Stefano Pirandola. “Continuous-variable measurement-device-independent quantum key distribution: Composable security against coherent attacks”. Phys. Rev. A 97, 052327 (2018).
https://doi.org/10.1103/PhysRevA.97.052327
[37] Shouvik Ghorai, Eleni Diamanti, and Anthony Leverrier. “Composable security of two-way continuous-variable quantum key distribution without active symmetrization”. Phys. Rev. A 99, 012311 (2019).
https://doi.org/10.1103/PhysRevA.99.012311
[38] Paul Jouguet, Sébastien Kunz-Jacques, Eleni Diamanti, and Anthony Leverrier. “Analysis of imperfections in practical continuous-variable quantum key distribution”. Phys. Rev. A 86, 032309 (2012).
https://doi.org/10.1103/PhysRevA.86.032309
[39] Cosmo Lupo. “Towards practical security of continuous-variable quantum key distribution”. Phys. Rev. A 102, 022623 (2020).
https://doi.org/10.1103/PhysRevA.102.022623
[40] Takaya Matsuura, Kento Maeda, Toshihiko Sasaki, and Masato Koashi. “Finite-size security of continuous-variable quantum key distribution with digital signal processing”. Nature Communications 12, 252 (2021).
https://doi.org/10.1038/s41467-020-19916-1
[41] Shinichiro Yamano, Takaya Matsuura, Yui Kuramochi, Toshihiko Sasaki, and Masato Koashi. “Finite-size security proof of binary-modulation continuous-variable quantum key distribution using only heterodyne measurement” (2022). arXiv:2208.11983.
arXiv:2208.11983
[42] Stefan Bäuml, Carlos Pascual García, Victoria Wright, Omar Fawzi, and Antonio Acín. “Security of discrete-modulated continuous-variable quantum key distribution” (2023). arXiv:2303.09255.
arXiv:2303.09255
[43] Cosmo Lupo and Yingkai Ouyang. “Quantum Key Distribution with Nonideal Heterodyne Detection: Composable Security of Discrete-Modulation Continuous-Variable Protocols”. PRX Quantum 3, 010341 (2022).
https://doi.org/10.1103/PRXQuantum.3.010341
[44] Peter W. Shor and John Preskill. “Simple Proof of Security of the BB84 Quantum Key Distribution Protocol”. Phys. Rev. Lett. 85, 441–444 (2000).
https://doi.org/10.1103/PhysRevLett.85.441
[45] Hoi-Kwong Lo and H. F. Chau. “Unconditional Security of Quantum Key Distribution over Arbitrarily Long Distances”. Science 283, 2050–2056 (1999).
https://doi.org/10.1126/science.283.5410.2050
[46] RENATO RENNER. “SECURITY OF QUANTUM KEY DISTRIBUTION”. International Journal of Quantum Information 06, 1–127 (2008).
https://doi.org/10.1142/S0219749908003256
[47] M Koashi. “Simple security proof of quantum key distribution based on complementarity”. New Journal of Physics 11, 045018 (2009).
https://doi.org/10.1088/1367-2630/11/4/045018
[48] Toyohiro Tsurumaru. “Equivalence of Three Classical Algorithms With Quantum Side Information: Privacy Amplification, Error Correction, and Data Compression”. IEEE Transactions on Information Theory 68, 1016–1031 (2022).
https://doi.org/10.1109/TIT.2021.3126160
[49] Masahito Hayashi and Toyohiro Tsurumaru. “Concise and tight security analysis of the Bennett-Brassard 1984 protocol with finite key lengths”. New Journal of Physics 14, 093014 (2012).
https://doi.org/10.1088/1367-2630/14/9/093014
[50] Toyohiro Tsurumaru. “Leftover Hashing From Quantum Error Correction: Unifying the Two Approaches to the Security Proof of Quantum Key Distribution”. IEEE Transactions on Information Theory 66, 3465–3484 (2020).
https://doi.org/10.1109/TIT.2020.2969656
[51] Stefano Pirandola, Riccardo Laurenza, Carlo Ottaviani, and Leonardo Banchi. “Fundamental limits of repeaterless quantum communications”. Nature Communications 8, 15043 (2017).
https://doi.org/10.1038/ncomms15043
[52] Jérôme Lodewyck, Matthieu Bloch, Raúl García-Patrón, Simon Fossier, Evgueni Karpov, Eleni Diamanti, Thierry Debuisschert, Nicolas J. Cerf, Rosa Tualle-Brouri, Steven W. McLaughlin, and Philippe Grangier. “Quantum key distribution over $25phantom{rule{0.3em}{0ex}}mathrm{km}$ with an all-fiber continuous-variable system”. Phys. Rev. A 76, 042305 (2007).
https://doi.org/10.1103/PhysRevA.76.042305
[53] Paul Jouguet, David Elkouss, and Sébastien Kunz-Jacques. “High-bit-rate continuous-variable quantum key distribution”. Phys. Rev. A 90, 042329 (2014).
https://doi.org/10.1103/PhysRevA.90.042329
[54] Xuan Wen, Qiong Li, Haokun Mao, Xiaojun Wen, and Nan Chen. “Rotation Based Slice Error Correction Protocol for Continuous-variable Quantum Key Distribution and its Implementation with Polar Codes” (2021). arXiv:2106.06206.
arXiv:2106.06206
[55] Karol Horodecki, Debbie Leung, Hoi-Kwong Lo, and Jonathan Oppenheim. “Quantum Key Distribution Based on Arbitrarily Weak Distillable Entangled States”. Phys. Rev. Lett. 96, 070501 (2006).
https://doi.org/10.1103/PhysRevLett.96.070501
[56] Joseph M. Renes and Graeme Smith. “Noisy Processing and Distillation of Private Quantum States”. Phys. Rev. Lett. 98, 020502 (2007).
https://doi.org/10.1103/PhysRevLett.98.020502
[57] K. Horodecki, M. Horodecki, P. Horodecki, D. Leung, and J. Oppenheim. “Unconditional Privacy over Channels which Cannot Convey Quantum Information”. Phys. Rev. Lett. 100, 110502 (2008).
https://doi.org/10.1103/PhysRevLett.100.110502
[58] Karol Horodecki, Michal Horodecki, Pawel Horodecki, and Jonathan Oppenheim. “General Paradigm for Distilling Classical Key From Quantum States”. IEEE Transactions on Information Theory 55, 1898–1929 (2009).
https://doi.org/10.1109/TIT.2008.2009798
[59] J. Eli Bourassa, Ignatius William Primaatmaja, Charles Ci Wen Lim, and Hoi-Kwong Lo. “Loss-tolerant quantum key distribution with mixed signal states”. Phys. Rev. A 102, 062607 (2020).
https://doi.org/10.1103/PhysRevA.102.062607
[60] Takaya Matsuura, Toshihiko Sasaki, and Masato Koashi. “Refined security proof of the round-robin differential-phase-shift quantum key distribution and its improved performance in the finite-sized case”. Phys. Rev. A 99, 042303 (2019).
https://doi.org/10.1103/PhysRevA.99.042303
[61] Takaya Matsuura. “Digital quantum information processing with continuous-variable systems”. Springer Nature. (2023). url: https://doi.org/10.1007/978-981-19-8288-0.
https://doi.org/10.1007/978-981-19-8288-0
[62] Thomas M. Cover and Joy A. Thomas. “Elements of Information Theory (Wiley Series in Telecommunications and Signal Processing)”. Wiley-Interscience. USA (2006).
[63] Toyohiro Tsurumaru and Masahito Hayashi. “Dual Universality of Hash Functions and Its Applications to Quantum Cryptography”. IEEE Transactions on Information Theory 59, 4700–4717 (2013).
https://doi.org/10.1109/TIT.2013.2250576
[64] Wassily Hoeffding. “Probability Inequalities for Sums of Bounded Random Variables”. Journal of the American Statistical Association 58, 13–30 (1963).
https://doi.org/10.2307/2282952
[65] Go Kato. “Concentration inequality using unconfirmed knowledge” (2020). arXiv:2002.04357.
arXiv:2002.04357
[66] Kazuoki Azuma. “Weighted sums of certain dependent random variables”. Tohoku Mathematical Journal 19, 357 – 367 (1967).
https://doi.org/10.2748/tmj/1178243286
[67] Hongyi Zhou, Toshihiko Sasaki, and Masato Koashi. “Numerical method for finite-size security analysis of quantum key distribution”. Phys. Rev. Res. 4, 033126 (2022).
https://doi.org/10.1103/PhysRevResearch.4.033126
[68] Jörn Müller-Quade and Renato Renner. “Composability in quantum cryptography”. New Journal of Physics 11, 085006 (2009).
https://doi.org/10.1088/1367-2630/11/8/085006
[69] V. Chvátal. “The tail of the hypergeometric distribution”. Discrete Mathematics 25, 285–287 (1979).
https://doi.org/10.1016/0012-365X(79)90084-0
[70] Maxim Raginsky and Igal Sason. “Concentration of Measure Inequalities in Information Theory, Communications, and Coding”. Foundations and Trends® in Communications and Information Theory 10, 1–246 (2013).
https://doi.org/10.1561/0100000064
[71] Colin McDiarmid. “Concentration”. Pages 195–248. Springer Berlin Heidelberg. Berlin, Heidelberg (1998).
https://doi.org/10.1007/978-3-662-12788-9_6
[72] Roger A. Horn and Charles R. Johnson. “Matrix Analysis”. Cambridge University Press. (1985).
https://doi.org/10.1017/CBO9780511810817
[73] M. L. Overton and R. S. Womersley. “Optimality conditions and duality theory for minimizing sums of the largest eigenvalues of symmetric matrices”. Mathematical Programming 62, 321–357 (1993).
https://doi.org/10.1007/BF01585173
Cited by
[1] Stefan Bäuml, Carlos Pascual García, Victoria Wright, Omar Fawzi, and Antonio Acín, “Security of discrete-modulated continuous-variable quantum key distribution”, arXiv:2303.09255, (2023).
[2] Shinichiro Yamano, Takaya Matsuura, Yui Kuramochi, Toshihiko Sasaki, and Masato Koashi, “General treatment of Gaussian trusted noise in continuous variable quantum key distribution”, arXiv:2305.17684, (2023).
The above citations are from SAO/NASA ADS (last updated successfully 2023-08-30 02:31:37). The list may be incomplete as not all publishers provide suitable and complete citation data.
On Crossref’s cited-by service no data on citing works was found (last attempt 2023-08-30 02:31:36).
This Paper is published in Quantum under the Creative Commons Attribution 4.0 International (CC BY 4.0) license. Copyright remains with the original copyright holders such as the authors or their institutions.
- SEO Powered Content & PR Distribution. Get Amplified Today.
- PlatoData.Network Vertical Generative Ai. Empower Yourself. Access Here.
- PlatoAiStream. Web3 Intelligence. Knowledge Amplified. Access Here.
- PlatoESG. Automotive / EVs, Carbon, CleanTech, Energy, Environment, Solar, Waste Management. Access Here.
- PlatoHealth. Biotech and Clinical Trials Intelligence. Access Here.
- ChartPrime. Elevate your Trading Game with ChartPrime. Access Here.
- BlockOffsets. Modernizing Environmental Offset Ownership. Access Here.
- Source: https://quantum-journal.org/papers/q-2023-08-29-1095/
- :has
- :is
- :not
- ][p
- 06
- 1
- 10
- 100
- 11
- 118
- 12
- 13
- 14
- 15%
- 16
- 17
- 19
- 1949
- 1984
- 1985
- 1998
- 1999
- 20
- 2000
- 2001
- 2006
- 2008
- 2011
- 2012
- 2013
- 2014
- 2015
- 2016
- 2017
- 2018
- 2019
- 2020
- 2021
- 2022
- 2023
- 2050
- 22
- 23
- 24
- 25
- 26%
- 27
- 28
- 29
- 30
- 3000
- 31
- 32
- 33
- 36
- 39
- 40
- 49
- 50
- 51
- 54
- 60
- 66
- 67
- 7
- 70
- 72
- 8
- 9
- 98
- a
- above
- ABSTRACT
- access
- Achieve
- achieved
- Achieves
- active
- advantages
- affiliations
- against
- Alexander
- algorithms
- All
- American
- Amplification
- an
- Analyses
- analysis
- and
- Andrew
- Anthony
- applications
- applied
- approach
- approaches
- ARE
- AS
- Association
- assumed
- Attacks
- Aug
- author
- authors
- based
- BE
- been
- Bell
- Berlin
- BEST
- Bit
- Black
- boris
- Break
- Broken
- brown
- but
- by
- cambridge
- cannot
- capability
- carlos
- case
- Center
- certain
- Channel
- channels
- Charles
- chen
- codes
- Coding
- COHERENT
- Coin
- Collective
- comment
- Commons
- Communication
- Communications
- compatibility
- complete
- computation
- computer
- computer science
- conditions
- Conference
- continuous
- copyright
- cover
- cryptography
- Daniel
- data
- data processing
- David
- Debbie
- dependent
- Detection
- developed
- developing
- difficult
- digital
- discuss
- distance
- distinct
- distribution
- due
- e
- Engineering
- error
- established
- excess
- expected
- exploiting
- extend
- fails
- For
- found
- Foundations
- from
- full-fledged
- functions
- General
- George
- Gilles
- Go
- graduate
- harvard
- hash
- hashing
- here
- High
- holders
- However
- HTTPS
- i
- IEEE
- image
- implementation
- improved
- improvements
- in
- inequalities
- information
- institutions
- interesting
- International
- ITS
- JavaScript
- John
- Johnson
- jonathan
- journal
- Key
- keys
- knowledge
- known
- Lam
- large
- largest
- Last
- Leave
- Li
- License
- LIMIT
- limits
- lin
- Line
- lines
- List
- Long
- loss
- many
- mario
- mark
- mathematical
- mathematics
- max-width
- Maxim
- May..
- measure
- measurement
- Melbourne
- method
- minimizing
- mixed
- model
- Month
- Nature
- networks
- New
- Nicolas
- no
- Noise
- notably
- obtain
- obtained
- of
- offer
- omar
- on
- only
- open
- optimal
- or
- original
- Other
- our
- over
- pages
- Paper
- paradigm
- Parallel
- Paul
- performance
- Peter
- phase
- Philippe
- Physics
- ping
- plato
- Plato Data Intelligence
- PlatoData
- polar
- poor
- Practical
- press
- previous
- previously
- principle
- privacy
- private
- processing
- Programming
- proof
- proofs
- protocol
- protocols
- provide
- public
- Public Key
- published
- publisher
- publishers
- Quantum
- quantum cryptography
- quantum error correction
- quantum information
- R
- random
- Rate
- Rates
- real world
- realized
- recently
- reconciliation
- reduction
- references
- refined
- regime
- remains
- Reports
- requirement
- research
- result
- Results
- reverse
- ROSA
- s
- scales
- scaling
- School
- School of Engineering
- Science
- scientific
- Secret
- secure
- security
- sender
- Series
- shift
- Shor
- showed
- side
- Signal
- Simon
- simultaneously
- situation
- Slice
- smooth
- solid
- Space
- States
- statistical
- stefan
- Step
- steven
- studies
- Successfully
- such
- suitable
- sums
- system
- Systems
- Technical
- Technologies
- Technology
- telecommunications
- that
- The
- their
- theoretical
- theory
- they
- this
- three
- Thus
- Title
- to
- tokyo
- tolerance
- towards
- Transactions
- treatment
- trusted
- two
- ultimate
- Uncertainty
- unconditional
- under
- university
- University of Tokyo
- updated
- URL
- USA
- used
- using
- variable
- via
- Victoria
- volume
- von
- W
- want
- was
- Wave
- we
- which
- william
- with
- without
- works
- Wright
- X
- year
- zephyrnet
- Zhao