Bitcoin was officially launched in 2009 and since its inception, the concept of proof-of-work (PoW)consensus mechanism to secure decentralized cryptocurrencies against double-spend attacks, has been widely popular.
What Is Proof-Of-Work?
In the blockchain ecosystem, there is an important stakeholder named “Miners”. These miners are the ones who compete in the blockchain network to validate and create any new block which eventually becomes a part of the Block-Chain. Only one miner succeeds and wins a reward to mine the block, this mined block is then broadcasted among the network and the new state of the network is maintained.
Proof-Of-Work is nothing but a complex math’s puzzle which has to be solved fast by all the competitor miners, whoever manages to be the first one to solve this puzzle is rewarded and the transaction block become an integral part of the blockchain network holding the information which will now stay forever unchanged.
The core idea behind PoW is to make it prohibitively expensive for a hacker/attacker to rewrite the blockchain and reverse transactions that are already verified and added to the blockchain.
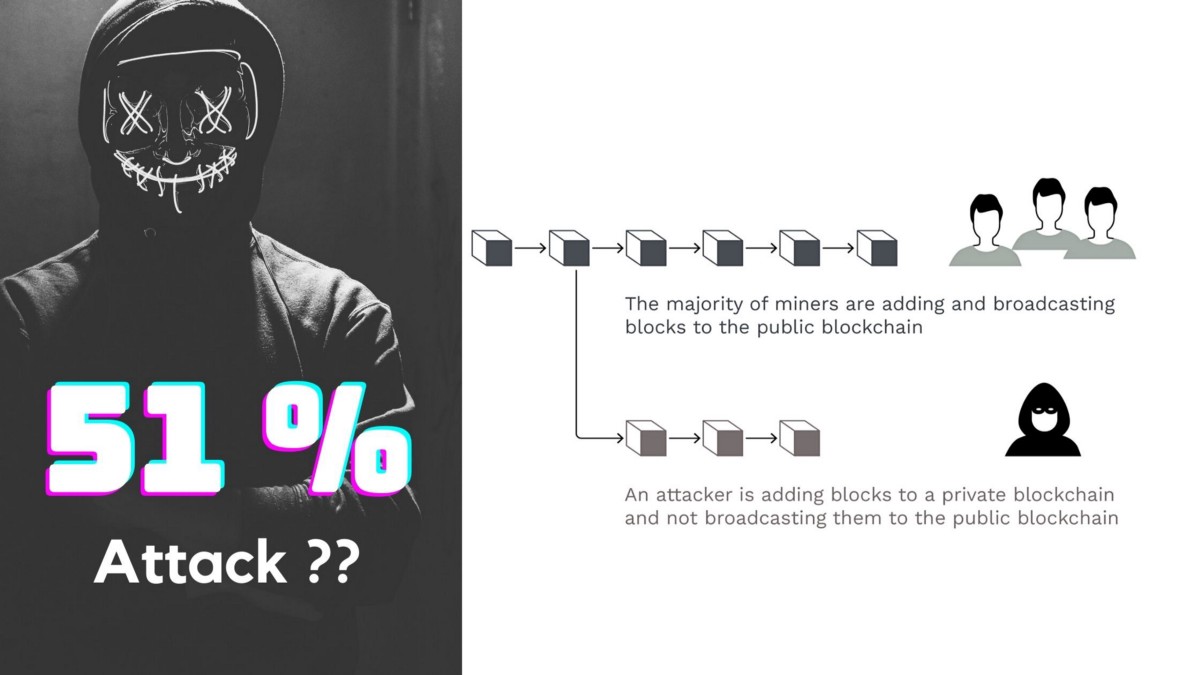
Well as discussed the attacker who intends to manipulate the transaction being performed over the blockchain has to ensure that it has the maximum control of the blockchain network’s mining hash rate, this can only be possible if an attacker or group of miners have more than 50% of the network’s mining hash rate or computing power under their control.
So, A 51% attack is an attack on a blockchain by a set of miners with malified intent to control more than 50% of the network’s mining hash rate. This gives them the power to play with the network and to interrupt the recording of new blocks by preventing other miners from finalizing the blocks.
What Can Go Wrong After 51 % attack?
If the set of miners or attackers successfully gain 51 % control of the blockchain network, they can enforce the following key damages
- They would be able to prevent any new transactions from attaining confirmations, allowing them to halt payments between some or all users.
- They may use this situation to activate double spending of coins, by reversing transactions that were completed while they were in control of the network
- They can prevent any other miners to perform the blockchain transaction validation and its finalization
In order to debunk 51 % attack functioning, we need to understand what is blockchain
The blockchain is the underlying tech behind bitcoin, Ethereum, Litecoin, and other altcoins. This blockchain is nothing but a distributed ledger (or database storage) that records every transaction made on a cryptocurrency’s network and are broadcasted to available to all users (network nodes )— and the general public — for review. This ensures that no single miner can spend a coin twice.
Let’s take the case of bitcoin which generates a new block approx. every 10 minutes. Once a block is finalized or mined, it cannot be altered since a fraudulent version of the public ledger would quickly be spotted and rejected by the network’s validators.
But hypothetically this fraud can happen, if the set of miner nodes comes together and manages to control the majority of the mining hash rate leading to a 51% attack. Thus by controlling the majority of the computing power on the network, an attacker or group of attackers can interfere with the process of recording & adding new blocks to the crypto network. They can take advantage of this monopoly and impact the mining of new blocks to maximize mining rewards in their favor
There has been quite a number of 51 % attack incident that has been reported in the recent past :
- Bitcoin SV attack of August 2021:
This is the latest incident that happened on the 4th of Aug 2021. Bloomberg reported that :
“Crypto Coin Bitcoin SV Appears to Have Faced a ‘51% Attack’. Refer to the tweet below which was posted by coin metrics :
2. Bitcoin Gold (BTG)Attack of May 2018:
In May 2018, Bitcoin Gold suffered a 51% attack. The attackers allegedly controlled a vast amount of Bitcoin Gold’s hash power, such that even with Bitcoin Gold repeatedly attempting to raise the exchange thresholds, the attackers were able to double-spend for several days, eventually stealing more than $18 million worth of Bitcoin Gold. Bitcoin Gold was hit again in 2020.
3. Krypton and Shift, an Ethereum, based blockchain suffered 51% attacks in August 2016.
4. Ethereum classics ETC, has also suffered a 51 % attack in the past multiple times. One such attack was reported by coindesk , where it stated that
- The Ethereum Classic blockchain has suffered a 51% attack Saturday evening, its third such attack this month, noticed by mining company Bitfly, which also spotted the first attack on Aug. 1.
- This attack reorganized over 7,000 blocks, or two days’ worth of mining, according to a tweet shared by Bitfly. The first two attacks reorganized 3,693 and 4,000 blocks respectively.
There are few strategies though not full-proof but still useful, that can be being employed to make such attacks difficult.
Some of the examples are :
1. Migrate To DPoS: Delegated Proof-Of- stake :
DPoS uses multiple delegates that change over time to validate each new block. In a DPoS blockchain, 51% of attackers must control both hashrate and the delegates, making attacks more difficult and unlikely. So one can migrate from PoW to this DPoS and minimize the risk.
2. Use Of MESS: Modified Exponential Subjective Scoring
MESS basically adds a “score”, called gravity, a requirement for any parallel reorg chain incoming to the network. This means that for all nodes present in the network, when they see a potential incoming reorg, they will compare it to the present chain from the point of the split, and arbitrarily demand an additional quantity of work to the incoming reorg chain.
This “gravity” quantity is negligible in the first few blocks of reorgs but increases exponentially as more blocks are reorganized. This is why it becomes very costly (exponentially) for attackers to reorg many blocks, as opposed to very cheap (linearly) without MESS.
So MESS can be employed that can analyze block reorganizations to assign a score that can indicate the trustworthiness of the reorganization.
MESS considers large-scale reorganizations, which underlie most 51% attacks, to be inherently untrustworthy.
The burgeoning ecosystem of cryptocurrency comes with its own set of opportunity and challenges, we as an investor has to work hard in increasing our awareness about all the crypto projects and spend good time to learn about their underlying tech and functioning, before jumping into investing on them.
The incidents like 51 % attack, rug-pull, double-spending are here to stay, but if we are acting in an informed manner we can be better prepared to minimize those risks and maximize our returns through smart crypto investing.
- &
- 000
- 2016
- 2020
- 51% attack
- 7
- 9
- Additional
- ADvantage
- All
- allegedly
- Allowing
- Altcoins
- among
- AUGUST
- Bitcoin
- Bitcoin Gold
- Bitcoin SV
- blockchain
- Bloomberg
- change
- Coin
- coin metrics
- Coindesk
- Coins
- company
- computing
- computing power
- considers
- crypto
- cryptocurrencies
- cryptocurrency
- Database
- decentralized
- Demand
- Distributed Ledger
- EC
- ecosystem
- ethereum
- Ethereum Classic
- exchange
- FAST
- First
- fraud
- General
- Gold
- good
- Group
- GV
- hash
- hash power
- hash rate
- Hashrate
- here
- How
- hr
- HTTPS
- ia
- idea
- Impact
- information
- intent
- investing
- investor
- IT
- Key
- latest
- leading
- LEARN
- Ledger
- Litecoin
- Majority
- Making
- medium
- Metrics
- million
- Miners
- Mining
- network
- nodes
- Opportunity
- order
- Other
- payments
- Popular
- PoW
- power
- present
- preventing
- projects
- Proof-of-Work
- public
- raise
- records
- returns
- reverse
- review
- Rewards
- Risk
- set
- shared
- smart
- So
- SOLVE
- spend
- Spending
- split
- stake
- State
- stay
- storage
- tech
- time
- transaction
- Transactions
- tweet
- users
- What is
- WHO
- Work
- worth













