1Institute for Quantum Computing and Department of Combinatorics and Optimization, University of Waterloo, Waterloo, Ontario N2L 3G1, Canada.
2Institute for Theoretical Physics, ETH Zürich, Switzerland.
3Institute for Quantum Computing and Department of Physics and Astronomy, University of Waterloo, Waterloo, Ontario N2L 3G1, Canada.
اس کاغذ کو دلچسپ لگتا ہے یا اس پر بات کرنا چاہتے ہیں؟ SciRate پر تبصرہ کریں یا چھوڑیں۔.
خلاصہ
We study the task of encryption with certified deletion (ECD) introduced by Broadbent and Islam (2020), but in a device-independent setting: we show that it is possible to achieve this task even when the honest parties do not trust their quantum devices. Moreover, we define security for the ECD task in a composable manner and show that our ECD protocol satisfies conditions that lead to composable security. Our protocol is based on device-independent quantum key distribution (DIQKD), and in particular the parallel DIQKD protocol based on the magic square non-local game, given by Jain, Miller and Shi (2020). To achieve certified deletion, we use a property of the magic square game observed by Fu and Miller (2018), namely that a two-round variant of the game can be used to certify deletion of a single random bit. In order to achieve certified deletion security for arbitrarily long messages from this property, we prove a parallel repetition theorem for two-round non-local games, which may be of independent interest.

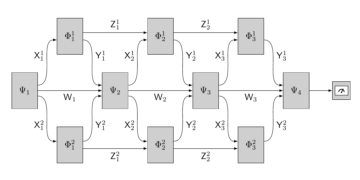
Featured image: Construction of simulator to prove composable security
► BibTeX ڈیٹا
► حوالہ جات
ہے [1] Nati Aharon, André Chailloux, Iordanis Kerenidis, Serge Massar, Stefano Pironio, and Jonathan Silman, “Weak coin flipping in a device-independent setting” Theory of Quantum Computation, Communication, and Cryptography 1-12 (2014).
https://doi.org/10.1007/978-3-642-54429-3_1
ہے [2] Rotem Arnon-Friedman, Frédéric Dupuis, Omar Fawzi, Renato Renner, and Thomas Vidick, "عملی ڈیوائس سے آزاد کوانٹم کرپٹوگرافی بذریعہ اینٹروپی جمع" نیچر کمیونیکیشنز 9, 459 (2018)۔
https://doi.org/10.1038/s41467-017-02307-4
https:///www.nature.com/articles/s41467-017-02307-4
ہے [3] Nati Aharon, Serge Massar, Stefano Pironio, and Jonathan Silman, “Device-independent bit commitment based on the CHSH inequality” New Journal of Physics 18, 025014 (2016).
https://doi.org/10.1088/1367-2630/18/2/025014
ہے [4] Charles H. Bennettand Gilles Brassard “Quantum cryptography: Public key distribution and coin tossing” Proceedings of International Conference on Computers, Systems and Signal Processing 175 (1984).
https://doi.org/10.1016/j.tcs.2011.08.039
ہے [5] جوناتھن بیریٹ، راجر کولبیک، اور ایڈرین کینٹ، "آلہ سے آزاد کوانٹم کرپٹوگرافی پر میموری کے حملے" فزیکل ریویو لیٹرز 110، 010503 (2013)۔
https:///doi.org/10.1103/PhysRevLett.110.010503
ہے [6] Anne Broadbentand Rabib Islam “Quantum Encryption with Certified Deletion” Theory of Cryptography 92–122 (2020).
https://doi.org/10.1007/978-3-030-64381-2_4
ہے [7] Michael Ben-Or, Michał Horodecki, Debbie W. Leung, Dominic Mayers, and Jonathan Oppenheim, “The Universal Composable Security of Quantum Key Distribution” Theory of Cryptography 386–406 (2005).
https://doi.org/10.1007/978-3-540-30576-7_21
ہے [8] Mohammad Bavarian, Thomas Vidick, and Henry Yuen, “Anchoring Games for Parallel Repetition” https://arxiv.org/abs/1509.07466 (2015).
https://arxiv.org/abs/1509.07466
ہے [9] Mohammad Bavarian, Thomas Vidick, and Henry Yuen, “Hardness Amplification for Entangled Games via Anchoring” Proceedings of the 49th Annual ACM SIGACT Symposium on Theory of Computing 303–316 (2017).
https://doi.org/10.1145/3055399.3055433
ہے [10] J. Lawrence Carterand Mark N. Wegman “Universal classes of hash functions” Journal of Computer and System Sciences 18, 143–154 (1979).
https://doi.org/10.1016/0022-0000(79)90044-8
ہے [11] Honghao Fuand Carl A. Miller “Local randomness: Examples and application” Physical Review A 97, 032324 (2018).
https:///doi.org/10.1103/PhysRevA.97.032324
ہے [12] Alexandru Gheorghiu, Tony Metger, and Alexander Poremba, “Quantum cryptography with classical communication: parallel remote state preparation for copy-protection, verification, and more” https://arxiv.org/abs/2201.13445 (2022).
https://arxiv.org/abs/2201.13445
ہے [13] Thomas Holenstein “Parallel Repetition: Simplifications and the No-Signaling Case” Proceedings of the Thirty-Ninth Annual ACM Symposium on Theory of Computing 411–419 (2007).
https://doi.org/10.1145/1250790.1250852
ہے [14] Rahul Jainand Srijita Kundu “A Direct Product Theorem for One-Way Quantum Communication” Proceedings of the 36th IEEE Annual Computational Complexity Conference (CCC 2021) 27:1–27:28 (2021).
https:///doi.org/10.4230/LIPIcs.CCC.2021.27
https://drops.dagstuhl.de/opus/volltexte/2021/14301
ہے [15] راہول جین، کارل اے ملر، اور یایوون شی، "متوازی ڈیوائس سے آزاد کوانٹم کلیدی تقسیم" آئی ای ای ای ٹرانزیکشنز آن انفارمیشن تھیوری 66، 5567–5584 (2020)۔
https:///doi.org/10.1109/TIT.2020.2986740
ہے [16] Rahul Jain, Attila Pereszlényi, and Penghui Yao, “A Parallel Repetition Theorem for Entangled Two-Player One-Round Games under Product Distributions” 2014 IEEE 29th Conference on Computational Complexity (CCC ’14) 209–216 (2014).
https:///doi.org/10.1109/CCC.2014.29
ہے [17] Julia Kempe, Hirotada Kobayashi, Keiji Matsumoto, Ben Toner, and Thomas Vidick, “Entangled Games are Hard to Approximate” 2008 49th Annual IEEE Symposium on Foundations of Computer Science 447–456 (2008).
https://doi.org/10.1109/FOCS.2008.8
ہے [18] Srijita Kundu, Jamie Sikora, and Ernest Y.-Z. Tan, “A device-independent protocol for XOR oblivious transfer” Quantum 6, 725 (2022).
https://doi.org/10.22331/q-2022-05-30-725
ہے [19] Srijita Kunduand Ernest Y.-Z. Tan “Device-independent uncloneable encryption” https://arxiv.org/abs/2210.01058 (2022).
https://arxiv.org/abs/2210.01058
ہے [20] Norbert Lütkenhaus, Ashutosh Marwah, and Dave Touchette, “Erasable Bit Commitment From Temporary Quantum Trust” IEEE Journal on Selected Areas in Information Theory 1, 536–554 (2020).
https://doi.org/10.1109/JSAIT.2020.3017054
ہے [21] Ueli Maurerand Renato Renner “Abstract Cryptography” The Second Symposium on Innovations in Computer Science, ICS 2011 1–21 (2011).
https://crypto.ethz.ch/publications/MauRen11.html
ہے [22] Stefano Pironio، Antonio Acín، Nicolas Brunner، Nicolas Gisin، Serge Massar، اور Valerio Scarani، "آلہ سے آزاد کوانٹم کلیدی تقسیم اجتماعی حملوں کے خلاف محفوظ" طبیعیات کا نیو جرنل 11، 045021 (2009)۔
https://doi.org/10.1088/1367-2630/11/4/045021
ہے [23] Christopher Portmannand Renato Renner “Cryptographic security of quantum key distribution” https://arxiv.org/abs/1409.3525 (2014).
https://arxiv.org/abs/1409.3525
ہے [24] Anup Rao “Parallel Repetition in Projection Games and a Concentration Bound” Proceedings of the Fortieth Annual ACM Symposium on Theory of Computing 1–10 (2008).
https://doi.org/10.1145/1374376.1374378
ہے [25] Ran Raz “A Parallel Repetition Theorem” Proceedings of the Twenty-Seventh Annual ACM Symposium on Theory of Computing 447–456 (1995).
https://doi.org/10.1145/225058.225181
ہے [26] ریناٹو رینر "کوانٹم کلیدی تقسیم کی حفاظت" تھیسس (2005)۔
https://doi.org/10.3929/ethz-a-005115027
ہے [27] Jonathan Silman, André Chailloux, Nati Aharon, Iordanis Kerenidis, Stefano Pironio, and Serge Massar, “Fully distrustful quantum bit commitment and coin flipping” Physical Review Letters 106, 220501 (2011).
https:///doi.org/10.1103/PhysRevLett.106.220501
ہے [28] Marco Tomamicheland Anthony Leverrier "کوانٹم کلید کی تقسیم کے لیے ایک بڑی حد تک خود ساختہ اور مکمل حفاظتی ثبوت" Quantum 1, 14 (2017)۔
https://doi.org/10.22331/q-2017-07-14-14
ہے [29] Dominique Unruh “Revocable Quantum Timed-Release Encryption” Advances in Cryptology – EUROCRYPT 2014 129–146 (2014).
https://doi.org/10.1007/978-3-642-55220-5_8
ہے [30] Bart van der Vecht, Xavier Coiteaux-Roy, and Boris Škorić, “Can’t Touch This: unconditional tamper evidence from short keys” https://arxiv.org/abs/2006.02476 (2020).
https://arxiv.org/abs/2006.02476
ہے [31] Thomas Vidick “Parallel DIQKD from parallel repetition” https://arxiv.org/abs/1703.08508 (2017).
https://arxiv.org/abs/1703.08508
ہے [32] Vilasini Venkatesh, Christopher Portmann, and Lídia del Rio, “Composable security in relativistic quantum cryptography” New Journal of Physics 21, 043057 (2019).
https://doi.org/10.1088/1367-2630/ab0e3b
ہے [33] Stephen Wiesner “Conjugate Coding” SIGACT News 15, 78–88 (1983).
https://doi.org/10.1145/1008908.1008920
کی طرف سے حوالہ دیا گیا
[1] Tony Metger, Omar Fawzi, David Sutter, and Renato Renner, “Generalised entropy accumulation”, آر ایکس سی: 2203.04989, (2022).
[2] Taiga Hiroka, Tomoyuki Morimae, Ryo Nishimaki, and Takashi Yamakawa، "تصدیق شدہ حذف کے ساتھ کوانٹم خفیہ کاری، نظر ثانی شدہ: عوامی کلید، انتساب پر مبنی، اور کلاسیکی مواصلات"، آر ایکس سی: 2105.05393, (2021).
[3] Taiga Hiroka, Tomoyuki Morimae, Ryo Nishimaki, and Takashi Yamakawa, “Certified Everlasting Functional Encryption”, آر ایکس سی: 2207.13878, (2022).
[4] Rahul Jain and Srijita Kundu, “A direct product theorem for quantum communication complexity with applications to device-independent cryptography”, آر ایکس سی: 2106.04299, (2021).
مذکورہ بالا اقتباسات سے ہیں۔ SAO/NASA ADS (آخری بار کامیابی کے ساتھ 2023-07-06 13:26:29)۔ فہرست نامکمل ہو سکتی ہے کیونکہ تمام ناشرین مناسب اور مکمل حوالہ ڈیٹا فراہم نہیں کرتے ہیں۔
نہیں لا سکا کراس ریف کا حوالہ دیا گیا ڈیٹا آخری کوشش کے دوران 2023-07-06 13:26:27: Crossref سے 10.22331/q-2023-07-06-1047 کے لیے حوالہ کردہ ڈیٹا حاصل نہیں کیا جا سکا۔ یہ عام بات ہے اگر DOI حال ہی میں رجسٹر کیا گیا ہو۔
یہ مقالہ کوانٹم میں کے تحت شائع کیا گیا ہے۔ Creative Commons انتساب 4.0 انٹرنیشنل (CC BY 4.0) لائسنس کاپی رائٹ اصل کاپی رائٹ ہولڈرز جیسے مصنفین یا ان کے اداروں کے پاس رہتا ہے۔
- SEO سے چلنے والا مواد اور PR کی تقسیم۔ آج ہی بڑھا دیں۔
- پلیٹو ڈیٹا ڈاٹ نیٹ ورک ورٹیکل جنریٹو اے آئی۔ اپنے آپ کو بااختیار بنائیں۔ یہاں تک رسائی حاصل کریں۔
- پلیٹوآئ اسٹریم۔ ویب 3 انٹیلی جنس۔ علم میں اضافہ۔ یہاں تک رسائی حاصل کریں۔
- پلیٹو ای ایس جی۔ آٹوموٹو / ای وی، کاربن، کلین ٹیک، توانائی ، ماحولیات، شمسی، ویسٹ مینجمنٹ یہاں تک رسائی حاصل کریں۔
- بلاک آفسیٹس۔ ماحولیاتی آفسیٹ ملکیت کو جدید بنانا۔ یہاں تک رسائی حاصل کریں۔
- ماخذ: https://quantum-journal.org/papers/q-2023-07-06-1047/
- : ہے
- : نہیں
- 1
- 10
- 11
- 12
- 13
- 14
- 15٪
- 16
- 17
- 19
- 1984
- 20
- 2005
- 2008
- 2011
- 2013
- 2014
- 2015
- 2016
- 2017
- 2018
- 2019
- 2020
- 2021
- 2022
- 22
- 23
- 24
- 25
- 26٪
- 27
- 28
- 29th
- 30
- 31
- 32
- 33
- 66
- 7
- 8
- 9
- a
- اوپر
- خلاصہ
- تک رسائی حاصل
- جمع کو
- حاصل
- ACM
- ایڈرین
- ترقی
- وابستگیاں
- کے خلاف
- الیگزینڈر
- تمام
- پروردن
- اور
- سالانہ
- انتھونی
- درخواست
- ایپلی کیشنز
- تخمینہ
- کیا
- علاقوں
- AS
- ھگول سائنس
- حملے
- مصنف
- مصنفین
- کی بنیاد پر
- BE
- بین
- بٹ
- بورس
- بنقی
- توڑ
- لیکن
- by
- کر سکتے ہیں
- کینیڈا
- ، کارل
- کیس
- CCC
- مصدقہ
- تصدیق کرنا
- چارلس
- کرسٹوفر
- کلاس
- کوڈنگ
- سکے
- اجتماعی
- تبصرہ
- وابستگی
- عمومی
- مواصلات
- کموینیکیشن
- مکمل
- پیچیدگی
- حساب
- کمپیوٹر
- کمپیوٹر سائنس
- کمپیوٹر
- کمپیوٹنگ
- دھیان
- حالات
- کانفرنس
- تعمیر
- کاپی رائٹ
- سکتا ہے
- کرپٹپٹ
- اعداد و شمار
- ڈیو
- ڈیوڈ
- ڈیبی
- شعبہ
- کے الات
- براہ راست
- بات چیت
- تقسیم
- تقسیم
- do
- کے دوران
- خفیہ کاری
- ETH
- بھی
- ثبوت
- مثال کے طور پر
- کے لئے
- بنیادیں
- سے
- fu
- فنکشنل
- افعال
- کھیل ہی کھیل میں
- کھیل
- Gilles کے
- دی
- ہارڈ
- ہارورڈ
- ہیش
- ہینری
- ہولڈرز
- HTML
- HTTPS
- IEEE
- if
- تصویر
- in
- آزاد
- معلومات
- بدعت
- اداروں
- دلچسپی
- دلچسپ
- بین الاقوامی سطح پر
- متعارف
- IT
- جیمی
- جاوا سکرپٹ
- جرنل
- کلیدی
- چابیاں
- بڑے پیمانے پر
- آخری
- لارنس
- قیادت
- چھوڑ دو
- لائسنس
- لسٹ
- لانگ
- ماجک
- انداز
- مارکو
- نشان
- زیادہ سے زیادہ چوڑائی
- مئی..
- پیغامات
- مائیکل
- ملر
- مہینہ
- زیادہ
- اس کے علاوہ
- یعنی
- فطرت، قدرت
- نئی
- خبر
- نکولس
- عام
- of
- عمر
- on
- اونٹاریو
- کھول
- اصلاح کے
- or
- حکم
- اصل
- ہمارے
- صفحات
- کاغذ.
- متوازی
- خاص طور پر
- جماعتوں
- جسمانی
- طبعیات
- پلاٹا
- افلاطون ڈیٹا انٹیلی جنس
- پلیٹو ڈیٹا
- ممکن
- تیاری
- کارروائییں
- پروسیسنگ
- مصنوعات
- پروجیکشن
- ثبوت
- جائیداد
- پروٹوکول
- ثابت کریں
- فراہم
- عوامی
- عوامی کلید
- شائع
- پبلیشر
- پبلشرز
- کوانٹم
- کمانٹم کمپیوٹنگ
- کوانٹم خفیہ نگاری
- بے ترتیب
- بے ترتیب پن
- حال ہی میں
- حوالہ جات
- رجسٹرڈ
- باقی
- ریموٹ
- کا جائزہ لینے کے
- سائنس
- سائنس
- دوسری
- محفوظ بنانے
- سیکورٹی
- منتخب
- قائم کرنے
- مختصر
- دکھائیں
- اشارہ
- سمیلیٹر
- ایک
- چوک میں
- حالت
- اسٹیفن
- مطالعہ
- کامیابی کے ساتھ
- اس طرح
- موزوں
- سوئٹزرلینڈ
- سمپوزیم
- کے نظام
- سسٹمز
- ٹاسک
- عارضی
- کہ
- ۔
- ان
- نظریاتی
- نظریہ
- مقالہ
- اس
- عنوان
- کرنے کے لئے
- ٹونی
- چھو
- معاملات
- منتقل
- بھروسہ رکھو
- غیر مشروط
- کے تحت
- یونیورسل
- یونیورسٹی
- اپ ڈیٹ
- URL
- استعمال کی شرائط
- استعمال کیا جاتا ہے
- مختلف
- توثیق
- کی طرف سے
- حجم
- W
- چاہتے ہیں
- تھا
- we
- جب
- جس
- ساتھ
- سال
- زیفیرنیٹ